Vulnerability Details Report - Applications
The Vulnerability Details Report includes detailed description of the vulnerabilities found in each application selected for this report, grouped by category, and includes for reference the code snippets associated with the vulnerabilities along with appropriate remediation instructions, followed by a list of the specific instances of that vulnerability found in the application code. This is an excellent report for helping developers remediate vulnerabilities, or providing an in-depth understanding of the specific vulnerabilities found for a particular asset.
Asset List
The Vulnerability Details Report provides a list of assets included in this report, shown below.
Issue Summary
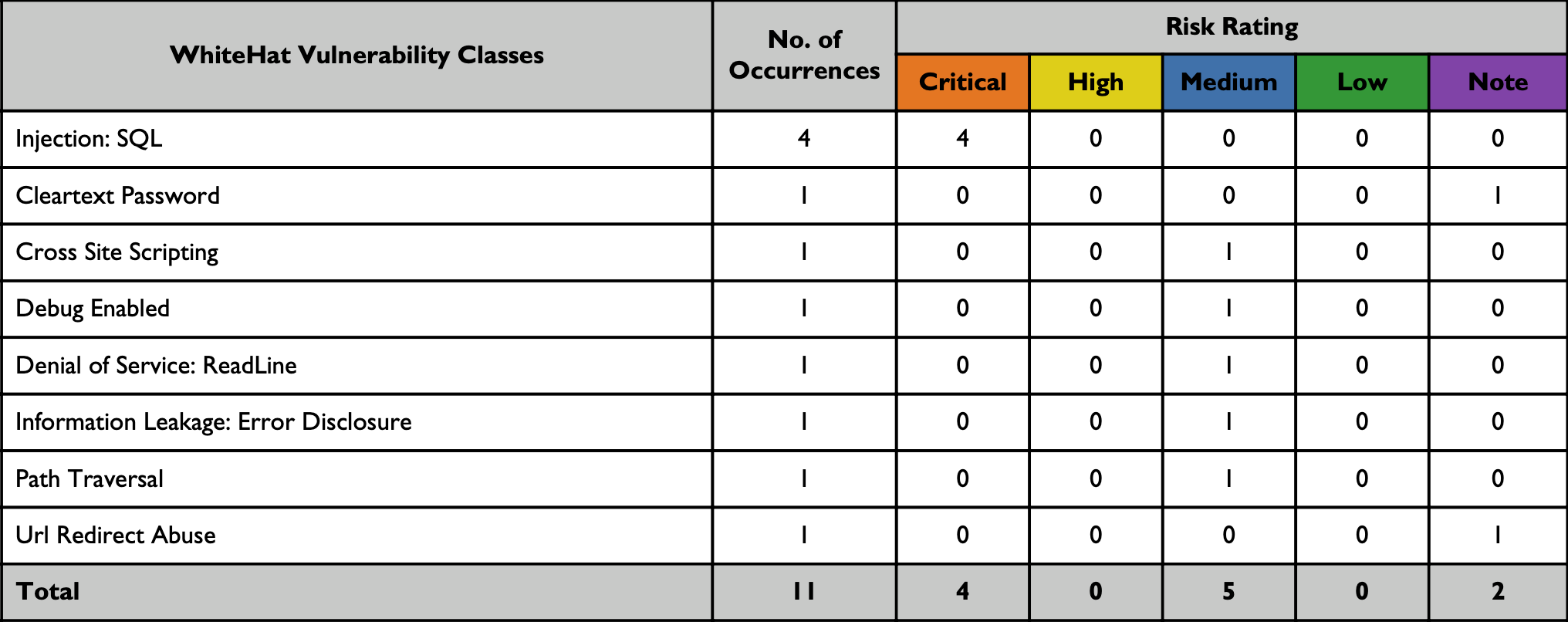
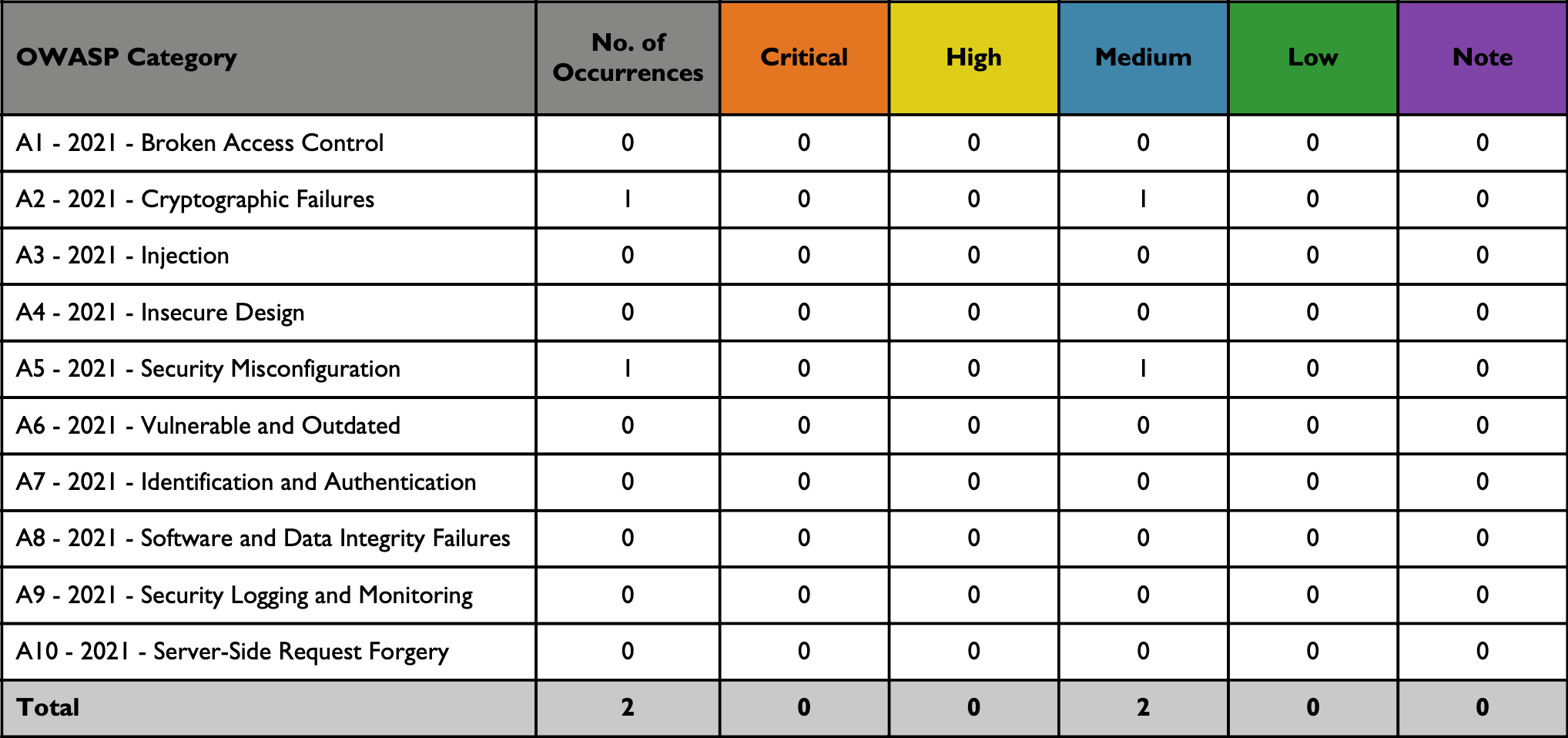
The following table summarizes open vulnerabilities by Continuous Dynamic vulnerability class across the application(s) included in this report. For your reference, the issue has been also broken up by Black Duck risk rating.
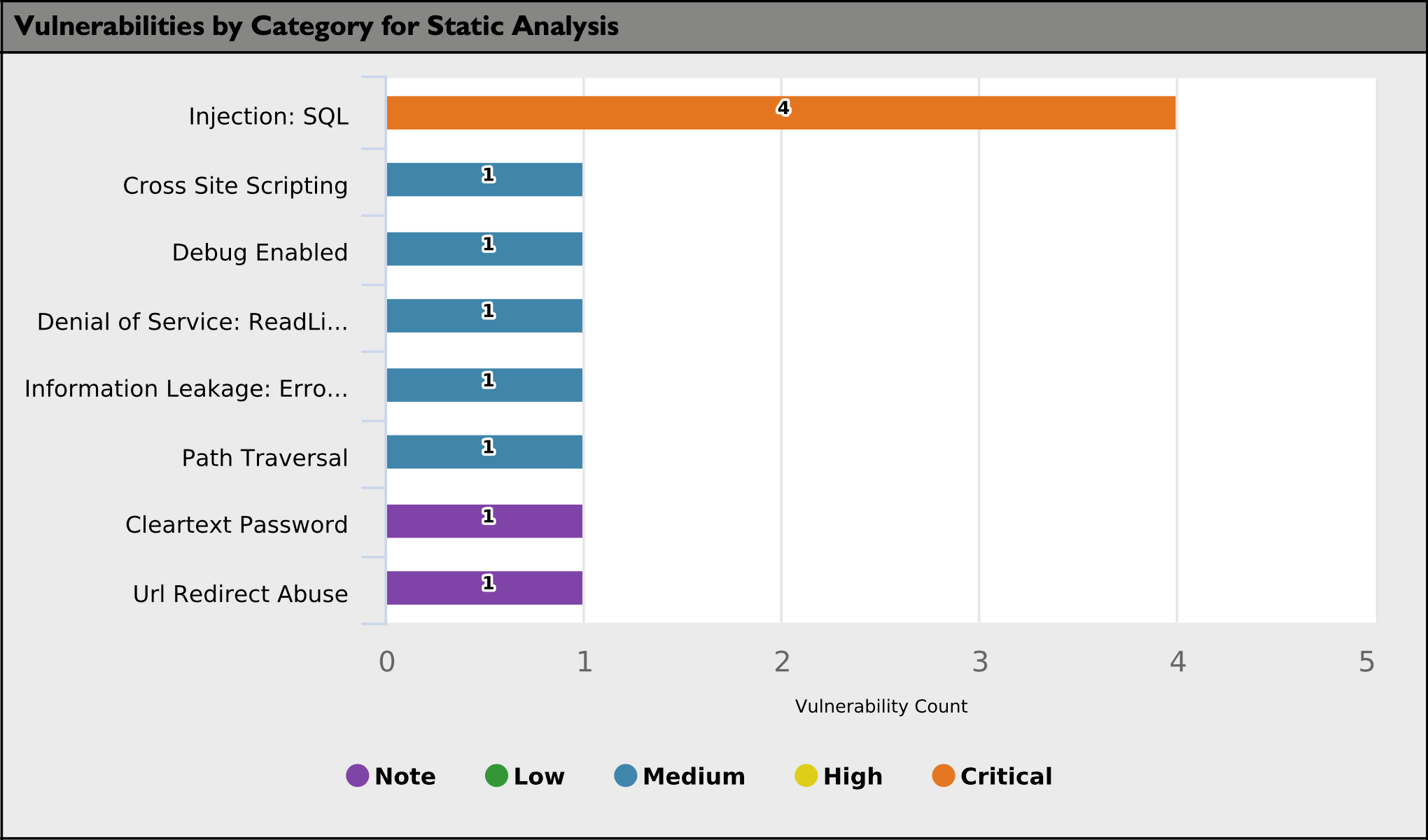
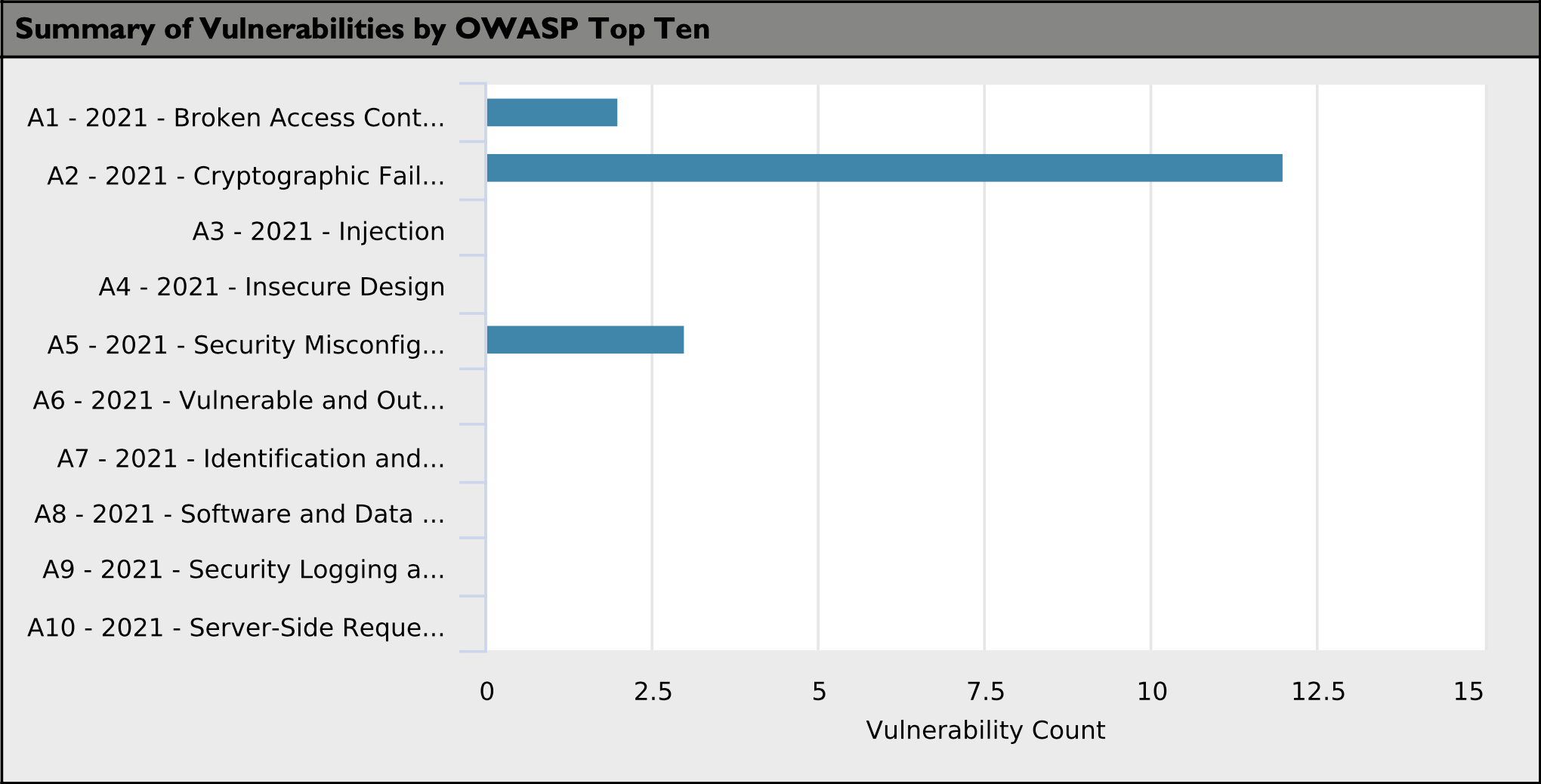
The following bar chart summarizes open vulnerabilities by Continuous Dynamic vulnerability class across the application(s) included in this report. For your reference, we have also indicated the risk ratings of the issues found in each vulnerability class.
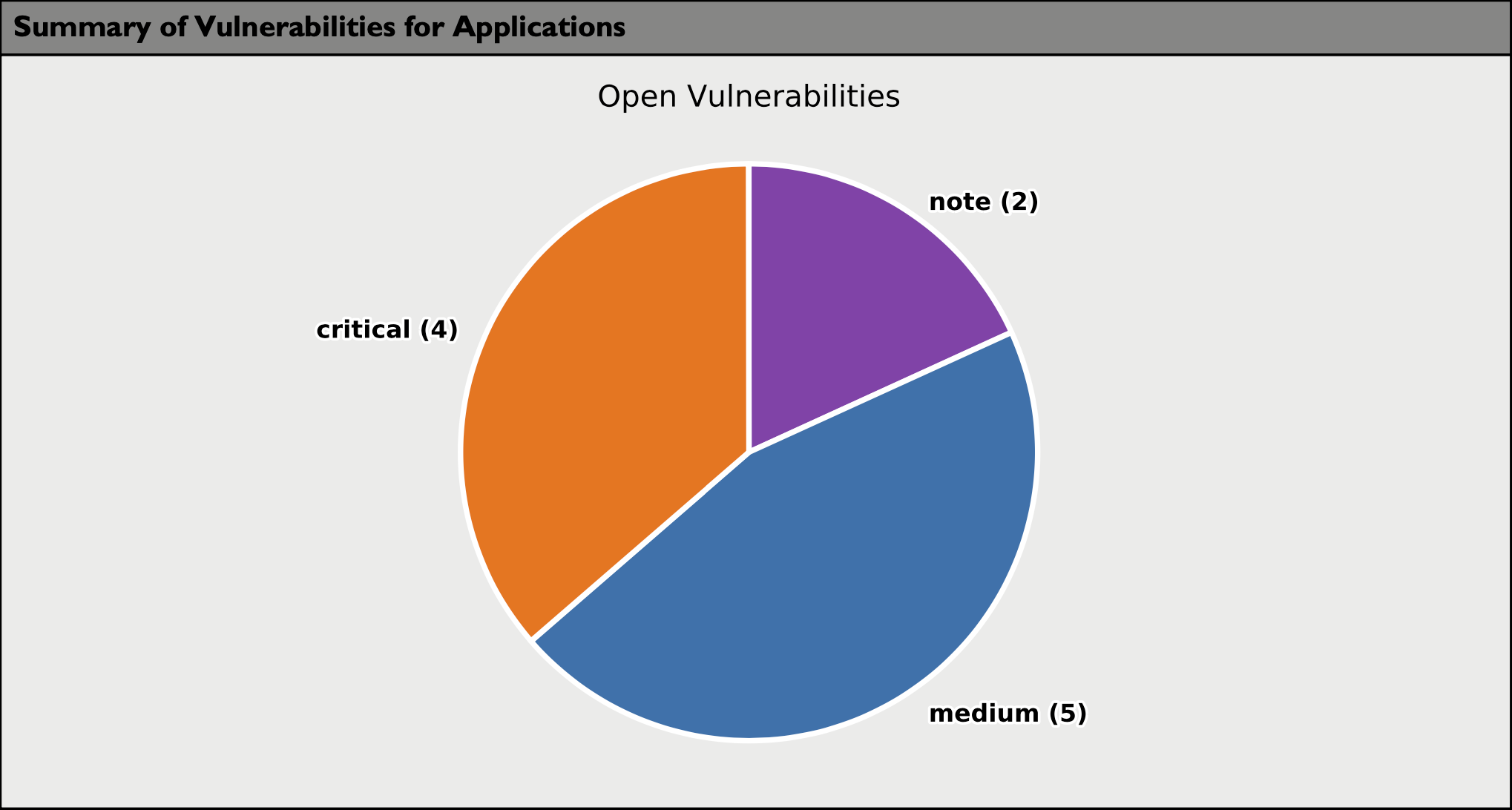
The following pie chart summarizes the number of open vulnerabilities by Black Duck risk rating across the application(s) included in this report.
The following table and bar chart summarizes the vulnerabilities found by Continuous Dynamic that also fall into the OWASP Top 10 Categories. Not all Continuous Dynamic vulnerability classes are represented in the OWASP Top 10 Categories, so not all vulnerabilities identified on your application(s) may be accounted for in this table.
| Some Continuous Dynamic vulnerability classes are associated with multiple OWASP Top 10 Categories, so a single vulnerability may appear more than once. For your reference, the issue has been also broken up by Continuous Dynamic risk rating. |
Report Sample
This report includes only the shortest attack vector for each vulnerability class identified during the assessment. In some cases, there may only be one attack vector. In other cases, there may be multiple attack vectors. The Developer Detailed Report contains all identified instances and attack vectors.
The Vulnerability Details Report provides descriptions and solutions for the following injections:
-
Environment Variable
-
Remote Code Execution
-
OS Command Injection
Injection: SQL
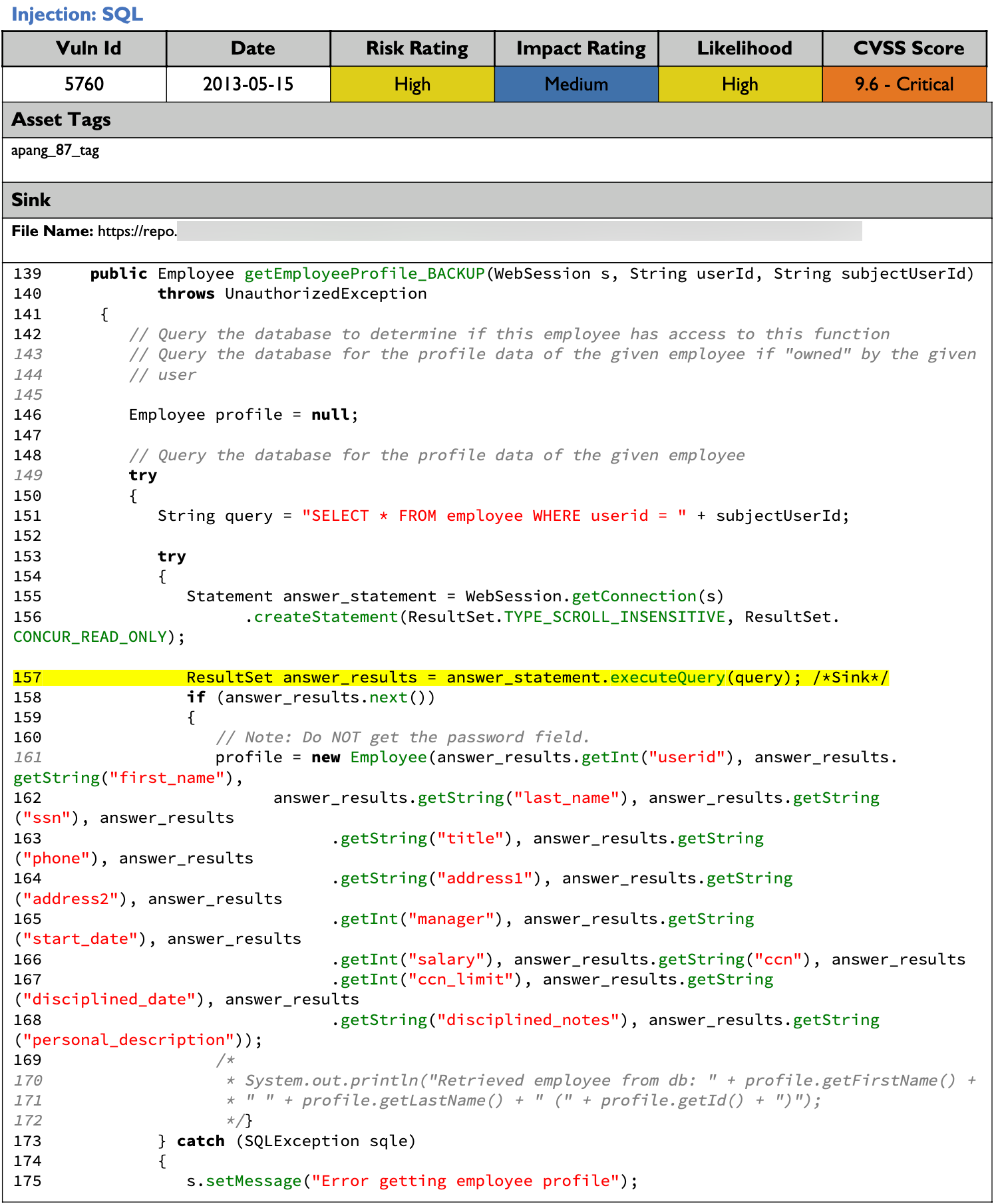
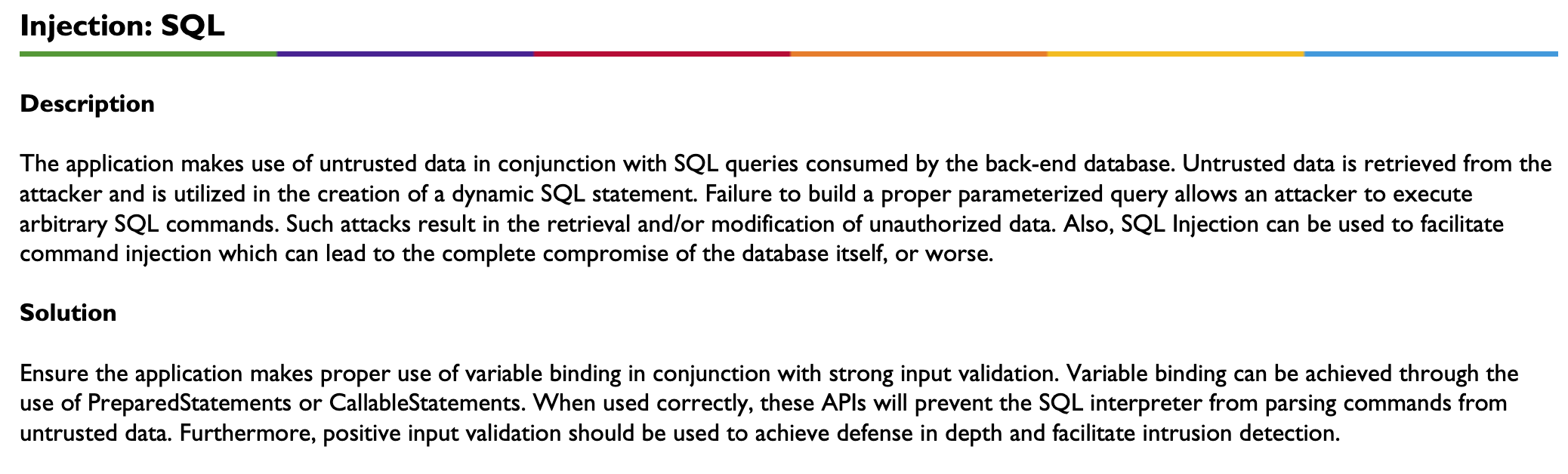
A Description of the vulnerability and how an attacker may exploit it is then provided along with a Solution on how to resolve the vulnerability.
Appendix - Vulnerability Level Definitions (by Risk)
This section details how the vulnerability levels are defined, risk Levels for the Sentinel Source solution are based on the OWASP risk rating methodology, based on the standard risk model (Risk = Likelihood x Impact) with several factors contributing to the likelihood and impact. The following tables show how the vulnerability ratings are calculated in The Vulnerability Details Report.
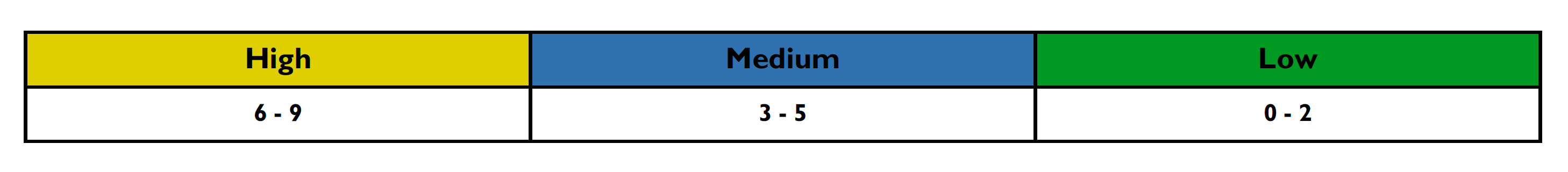
-
The Impact can be broken down into the Technical Impact and Business Impact. Technical impact considers the traditional areas of security: confidentiality, integrity, availability, and accountability.
-
The business impact stems from the technical impact and consider things such as: financial damage, reputational damage, non-compliance, and privacy violations.
After scoring the Likelihood and Impact, the Risk Rating is determined using the following table:
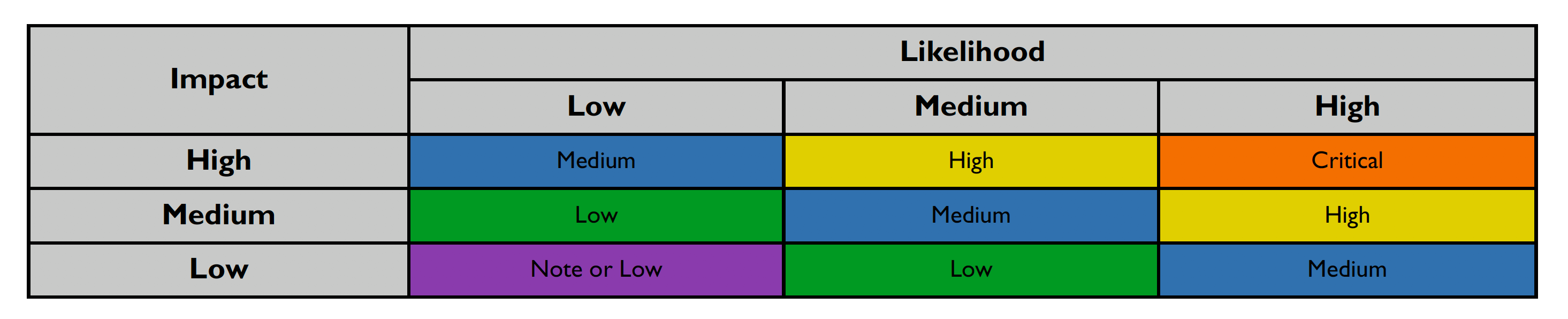
Risk ratings are defined below:
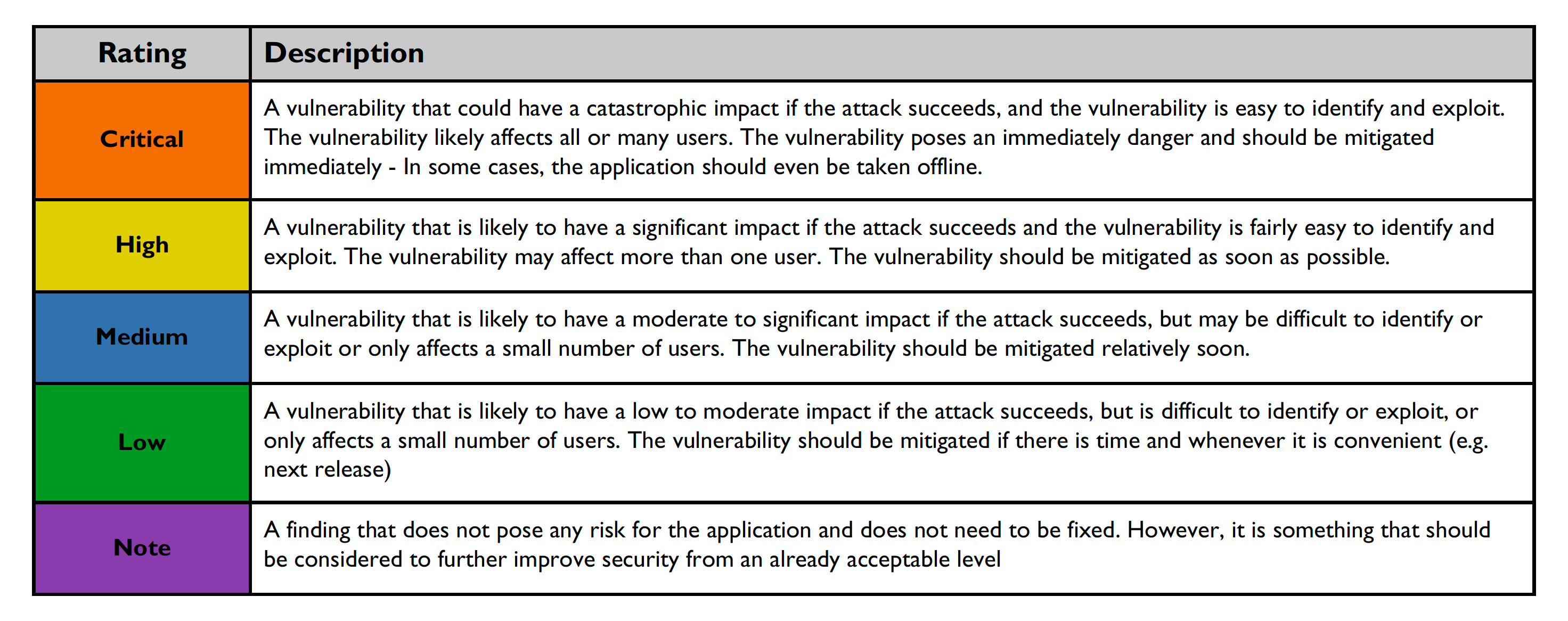
Vulnerability verification status indicated below: