Using Directed Remediation for Sentinel Source
Sentinel Source is used to analyze source code for security vulnerabilities. You have the ability to download a patch and associated library to remediate a given vulnerability.
| Continuous Dynamic Portal Administrators must have enabled Directed Remediation to use this function, see Enabling Directed Remediation for additional information. |
To view and identify vulnerabilities with direct remediation available, perform the following steps:
-
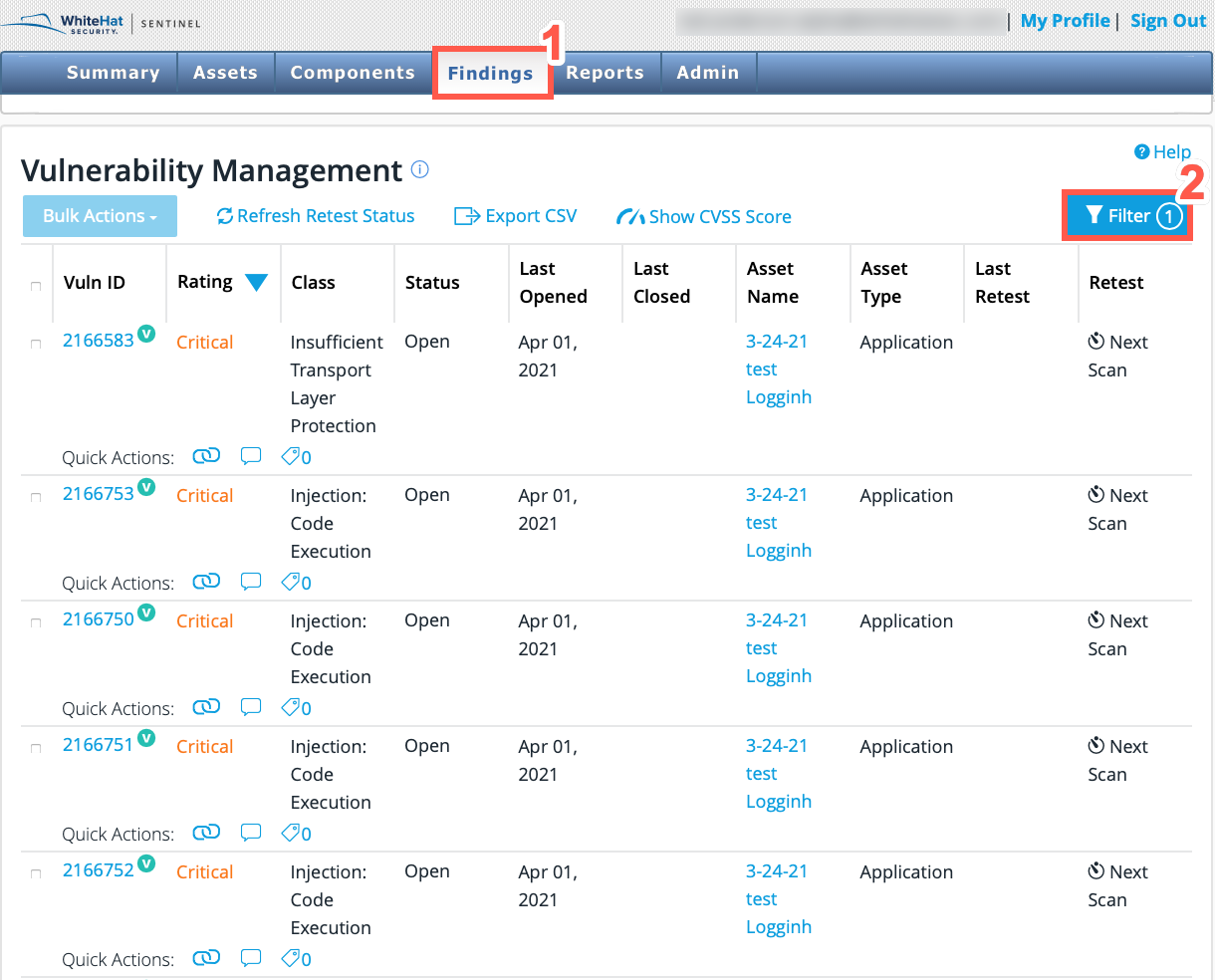
From the main Portal menu, click Findings.
-
Click on the Filter icon.
-
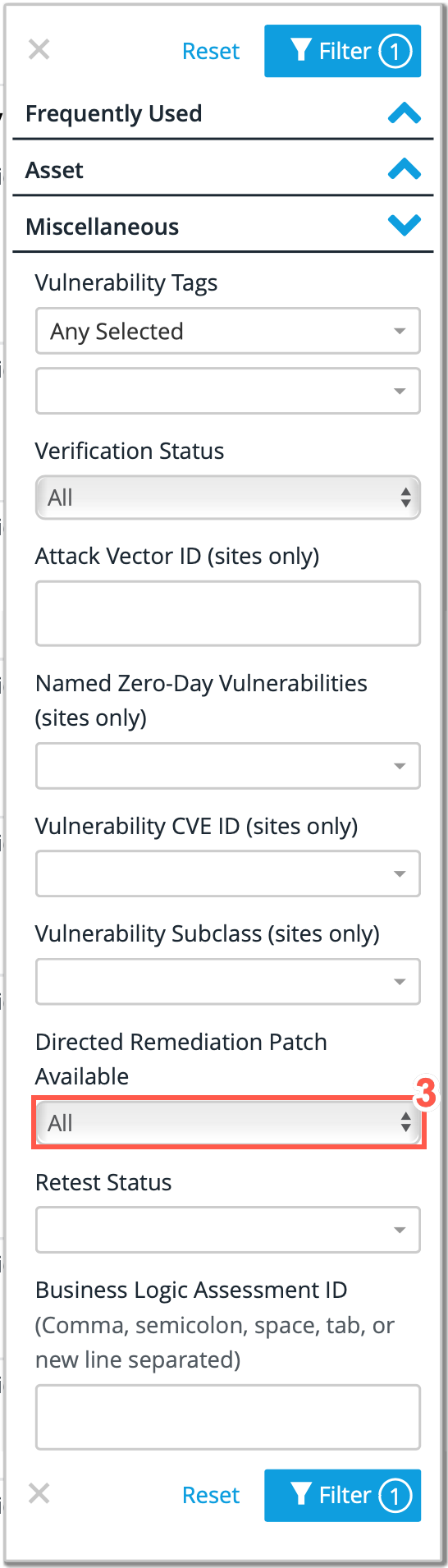
Click on the drop-down menu for Directed Remediation Patch Available.
-
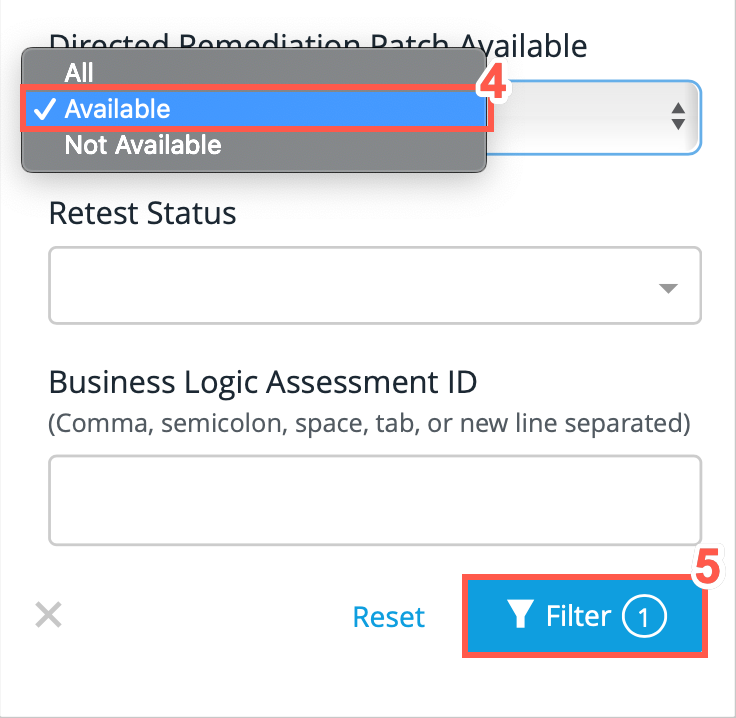
From the options available, select Available.
-
Click Filter to filter the Findings table.
-
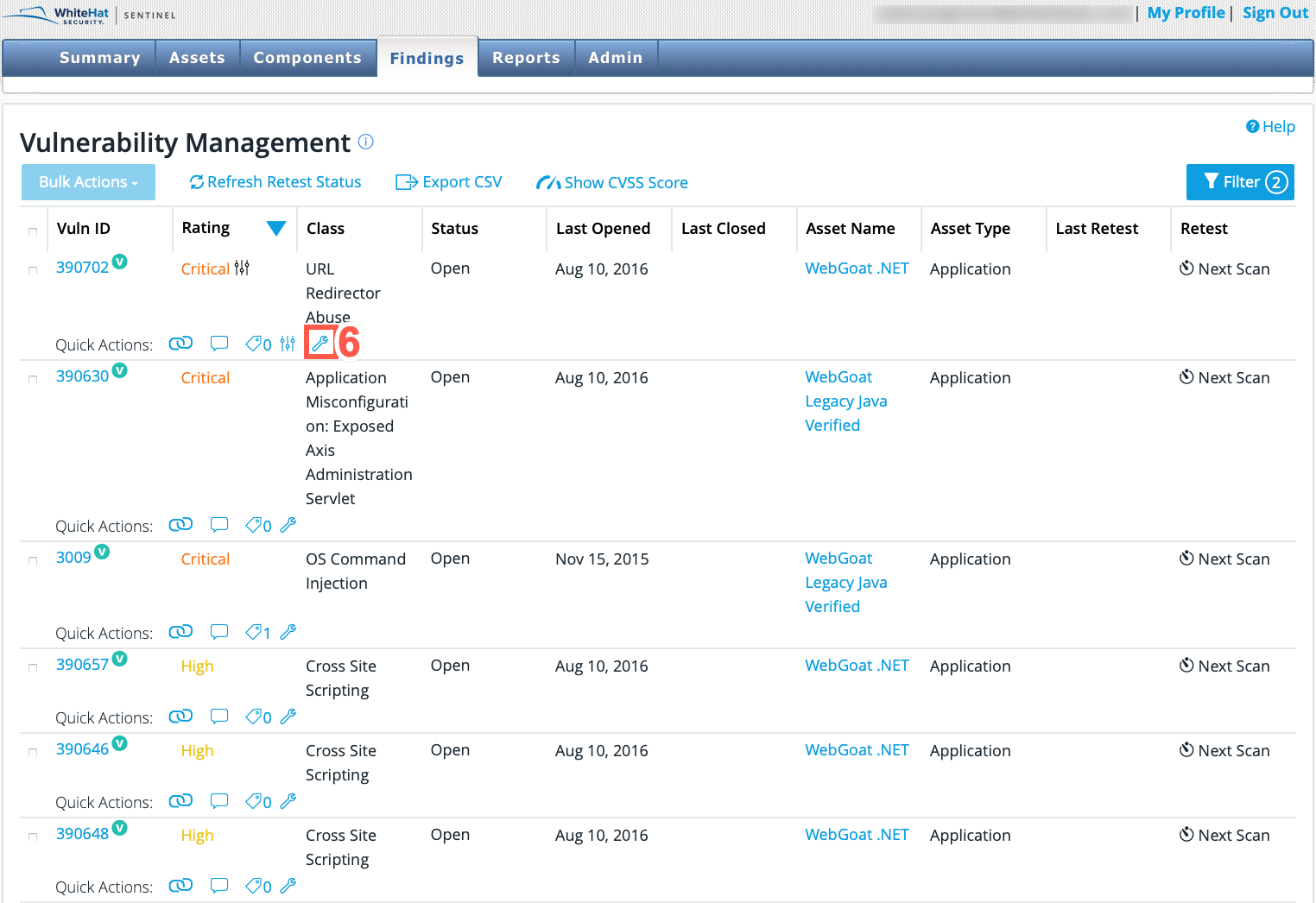
From the table of findings displayed, click the Wrench/Spanner icon beside the desired finding. This displays the Vulnerability Detail page.
-
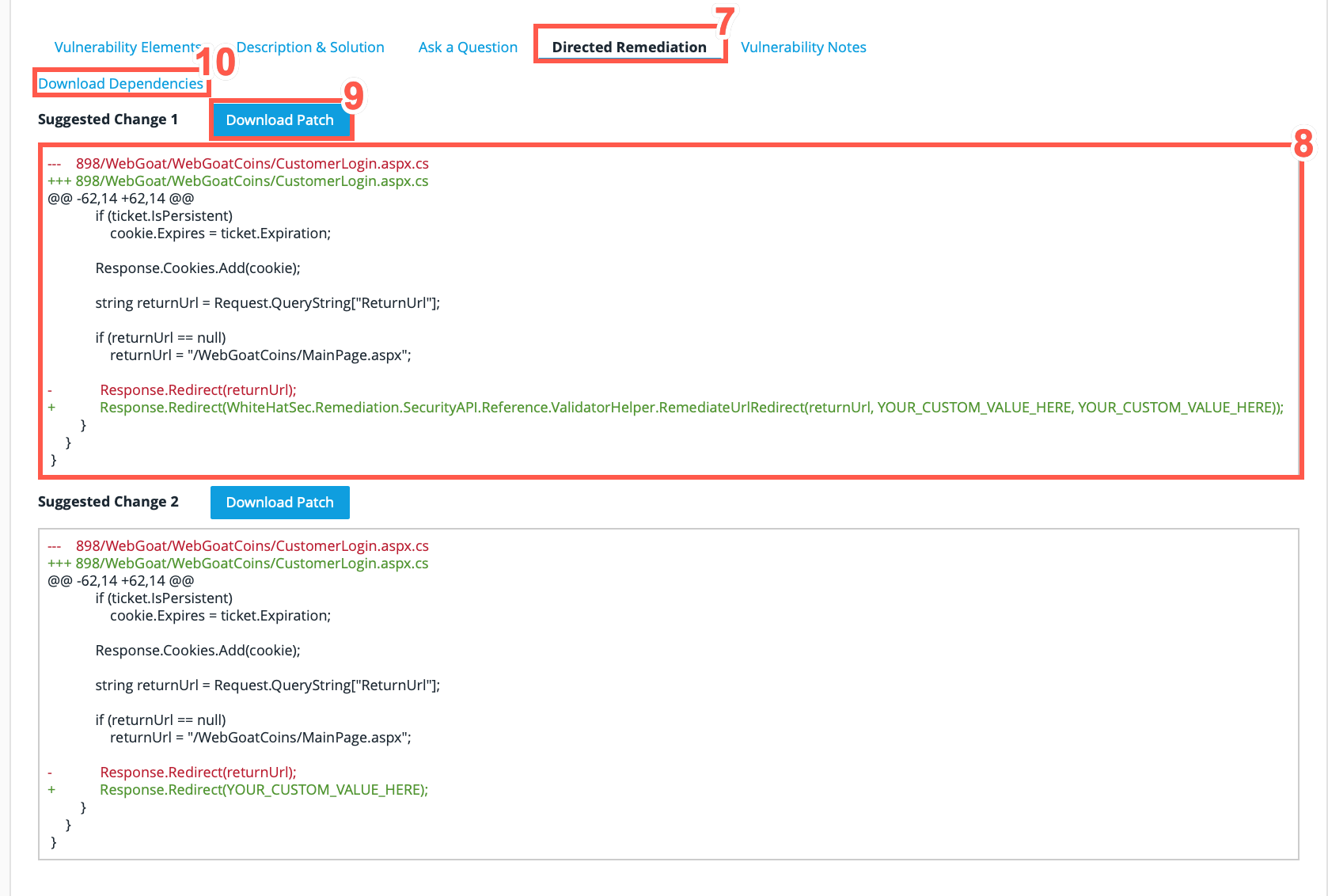
Select the Directed Remediation tab at the bottom of the Vulnerability Detail page.
-
Choose which of the Suggested Changes that you want to download.
-
Click Download Patch to begin the download.
-
Click on Download Dependencies. This is required to use the patch successfully, since the patch depends on a Black Duck library.
Alternatively, if you understand what is needed from reading the patch, you can correct your code directly and reference the libraries that you already have installed. See Using Directed Remediation - Libraries for additional information on downloading the library and incorporating it in your project.
To apply a patch that you have selected from Black Duck’s Directed Remediation, see Using Directed Remediation - Patches for more information.