The Continuous Dynamic Portal Menu - Findings
Click the Findings tab to show the Vulnerability Management page, which allows users to quickly determine which vulnerabilities on their assets require attention and track the success of their team’s remediation efforts. Users can also show or hide the CVSS score for vulnerabilities, refresh the Vuln Retest status, export the findings to a comma-delimited (CSV) file, or request vuln retests (individually or under the Bulk Actions button).
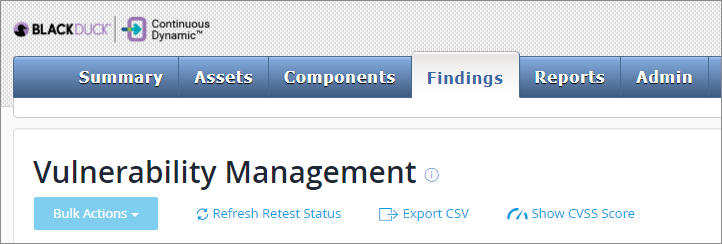
You can export the information on this page to a CSV file; clicking Refresh Retest Status will update the retest status of any vulnerability for which that status has been changed. Clicking Show CVSS Score will show the CVSS score for the vulnerabilities listed. For more information on CVSS scores, go to the National Vulnerability Database at the National Institute of Standards and Technology.
Each vulnerability is listed by Vuln ID, with a Quick Actions section available to allow users to view attack vectors (![]() ), notes (
), notes (![]() ), or tags (
), or tags (![]() ) associated with the vulnerability. Click the Vuln ID, as usual, for more details about the vulnerability.
) associated with the vulnerability. Click the Vuln ID, as usual, for more details about the vulnerability.
For more information about the Vulnerability Rating, how the rating is determined, and what it means, see How Your Vulnerability Ratings are Determined.
Vulnerability information given on the Findings page includes the following:
Vulnerability ID
The Vulnerability ID is a unique identifier for this specific instance of this vulnerability.
Rating
The vulnerability rating is an indicator of the level of risk associated with this vulnerability, based on the amount of damage that could be done if the vulnerability is exploited (impact), the ease with which it is possible to exploit this vulnerability (likelihood), and, if this vulnerability is found on a site and the customer has provided a priority value for the site, the priority. For more information, see "How Your Vulnerability Ratings are Determined." To customize the rating for a specific vulnerability or a class of vulnerabilities and an asset or assets, see "Customizing Your Vulnerability Results."
Class
The Vulnerability Class is the broad category of types of vulnerabilities to which this particular vulnerability belongs. For more information on Vulnerability Classes, see the glossary entry for the Vuln Class.
CVSS Score (if selected)
The CVSS Score is the "Common Vulnerability Scoring System" score for this vulnerability, based on any custom information you have entered and on the standard CVSS score for vulnerabilities of this class. For more information on the CVSS score, please see the Common Vulnerability Scoring System information available at https://www.first.org/cvss/.
Status
Status: the vulnerability status indicates whether the vulnerability is currently open, closed, accepted, out of scope, invalid, or mitigated.
Last Opened
Last Opened: indicates the date the vulnerability was last found and opened.
Last Closed
Last Closed: indicates the date as of which the vulnerability was found to have been remediated.
Asset Name
Asset Name: is the name of the asset where the vulnerability was located.
Asset Type
Asset Type: will be either "application" (code base or binary covered under Static Application Security Testing) or "site" (a pre-production or product site covered under Dynamic Application Security Testing).
Last Retest
The date the vulnerability was last retested.
Retest
The "Retest" column provides a link allowing you to request retesting for that specific vulnerability. To request retesting for multiple vulnerabilities, select the vulns using the checkbox to the left of the Vuln ID and use "Bulk Actions" to request the retest.
For more details on each individual vulnerability, click the Vuln ID and you will be taken to the appropriate Vulnerability Details Page; click the Asset Name to view asset details.
| For information on customizing individual vulnerabilities, see Customizing Risk Ratings for a Specific Vulnerability. To customize all vulnerabilities of a given class for specific assets, see Customizing Your Vulnerability Results. |
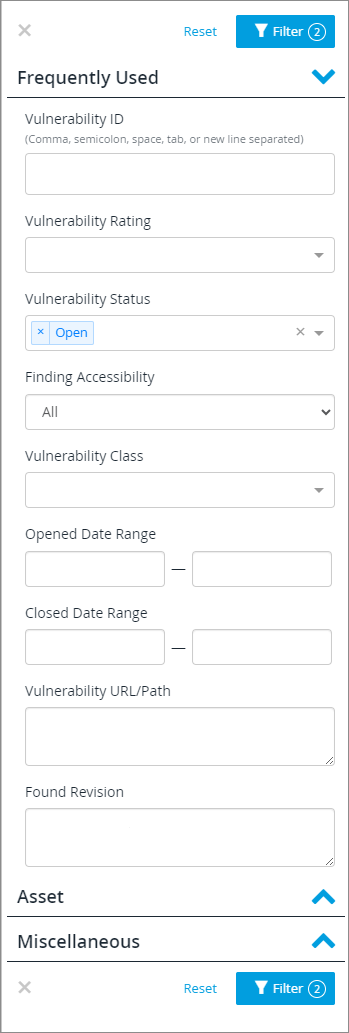
The filter is set to show only open vulns by default. To add or remove filters, click Filter ( ). You can filter by:
). You can filter by:
-
Frequently Used: The Vulnerability ID, rating, status, finding accessibility (accessible or unreachable), or vulnerability class; by date opened or closed (by date range), by vulnerability URL/path, or by found revision.
-
Asset: The asset name, type, status (active or inactive), service level, or the asset group name.
-
Miscellaneous: Vulnerability tags and verification status.
-
For Site assets, you can filter by attack vector ID, named zero-day vulnerabilities, vulnerability CVE or CWE ID, or vulnerability subclass.
-
For applications, you can filter by the availability of directed remediation patches.
-
Manually Discovered differentiates between vulnerabilities manually found in a Business Logic Assessment (BLA) and vulnerabilities found by the scanner.
-
You can also filter by client (for multi-client customers), retest status, or the ID of the Business Logic Assessment in which the vulnerability was found.
-
Each section of the filter can be expanded or closed for ease of use. If there are many possible values for a filter term, the filter box may scroll. If you do not see the value you want to filter on, be sure to scroll through the list or begin typing to see matching values.
To reset filters to their default values (only open vulns), click Reset.
The number of filters selected is shown on the filter button.
Filter selections are saved, as are the number of rows displayed, which will allow you to maintain your context and preferred view of the table between sessions. Filter selections are also reflected in the browser URL, so you can bookmark frequent selections and share them with others on your team.
If you have an unanswered question about a vulnerability, use Ask About a Vulnerability in the Continuous Dynamic Portal.