Setting up Time-based One-time Password (TOTP) MFA
Continuous Dynamic can perform authenticated scans of sites and web apps that use Time-based One-time Password (TOTP) multi-factor authentication (MFA). This is where a user authenticates by entering a TOTP token generated in a mobile app, like Google Authenticator, in addition to their username and password.
The DAST scanner features a proprietary MFA solution that automatically generates TOTP tokens for a correctly configured Site asset (a new token is generated every 30 seconds). This allows the scanner to automatically authenticate to the site and start a scan, simulating a user login through TOTP MFA.
Setup Overview
Configuring TOTP MFA is completely self-service through the Continuous Dynamic Portal by a Continuous Dynamic Admin. You do not need to open a Support case. When you have identified a site that uses TOTP MFA, you can simply add your Secret Key to the site’s scanning credentials. You can do this:
-
During DAST Onboarding—at any point after you create the asset in the Portal.
-
After onboarding, at any point in the asset’s lifecycle.
Once a Site asset is configured, a Black Duck Onboarding Support engineer must perform some internal configuration and manually verify the login process, as described in Verifying the TOTP MFA process.
MFA Provider Support Details
Continuous Dynamic supports authenticated site scans through several popular MFA providers, including:
-
Google Authenticator
-
Microsoft Authenticator
-
Duo Mobile
About Secret Keys
The MFA provider must require app developers to use a Secret Key. This a unique key used by your site to generate TOTP tokens for users, which they access through a mobile authenticator app. Your MFA provider should have given your unique Secret Key to your app developers.
Your MFA solution must use SHA-1 hashing and Base32 encoded Secret Keys. Secret keys retrieved from supported providers will already be in the correct format.
Note that authenticated scanning of TOTP MFA sites is not possible without access to your Secret Key.
Configuring a Site asset with your Secret Key
This task describes how to add your Secret Key to an existing set of scanning credentials for a site that uses TOTP MFA.
Prerequisites: You have added scanning credentials to the site.
-
Sign in to the Portal with a user account that has Administrator privileges.
-
Select Assets > Site Details.
-
Select a site from the list.
-
Under Credentials for Scanning, click the blue chevron
 to expand the scanning credentials.
to expand the scanning credentials. -
Click Edit.
-
For the Primary set of credentials, select the Enable Time-based One-time Password (TOTP) MFA checkbox.
-
Enter or paste your Secret Key in the TOTP Secret Key field.
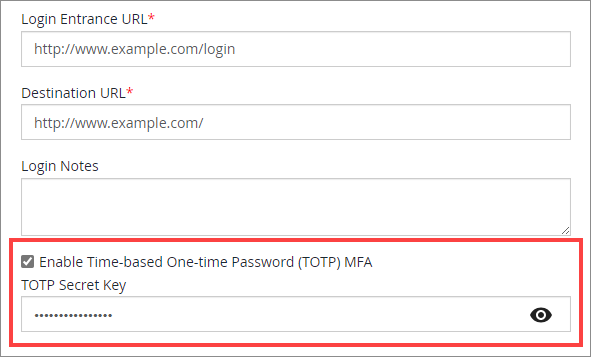
Check that the Secret Key is in all caps and does not contain spaces, e.g. WCUXRQCOKQJJWMPZ. Incorrect tokens might be generated if these requirements are not met, delaying your implementation. -
Repeat steps 4-7 for the Backup set of credentials.
-
Click Save.
A Black Duck Onboarding Support engineer can now securely access your Secret Key and verify the login process, as described in the next section.
Verifying the TOTP MFA process
Before the initial assessment can begin, a Black Duck Onboarding Support engineer must perform some internal configuration and verify the authentication process works as expected. They will do the following:
-
Manually authenticate to the site or web app with the provided scan credentials and the TOTP token (generated by the internal MFA solution using your Secret Key). The engineer will create a Support case if they encounter an issue, such as:
-
The site has become inaccessible.
-
The token is not being sent or received.
-
The authentication process is not working.
-
-
Configure the DAST scanner to generate the correct tokens and submit them appropriately during the login process.
When these steps are complete, the engineer will update the associated Support Case (if one exists).
Adding TOTP MFA to an existing Site asset
Setting up TOTP MFA is self-service throughout the lifecycle of an asset. To add the functionality to an existing Site asset:
-
Follow the steps in Configuring a Site asset with your Secret Key.
-
After you have added your Secret Key to the site’s scanning credentials, create a Support case to inform Black Duck Support engineers of the change.
Do not enter your Secret Key in the Support case or comments.
Next Steps
Your site or web app is now configured for authenticated scans using Time-based One-time Password multi-factor authentication. The DAST onboarding process can continue as described in the DAST Onboarding Overview.