The Asset Summary Report
The Asset Summary Report contains an overview of each asset’s vulnerabilities by category, as well as trends of vulnerabilities discovered by month over the past year. In addition, the report lists each asset’s vulnerabilities prioritized by their risk and severity level. The Asset Summary Report displays a summary of the open vulnerabilities for each asset in four sections.
Vulnerability Count
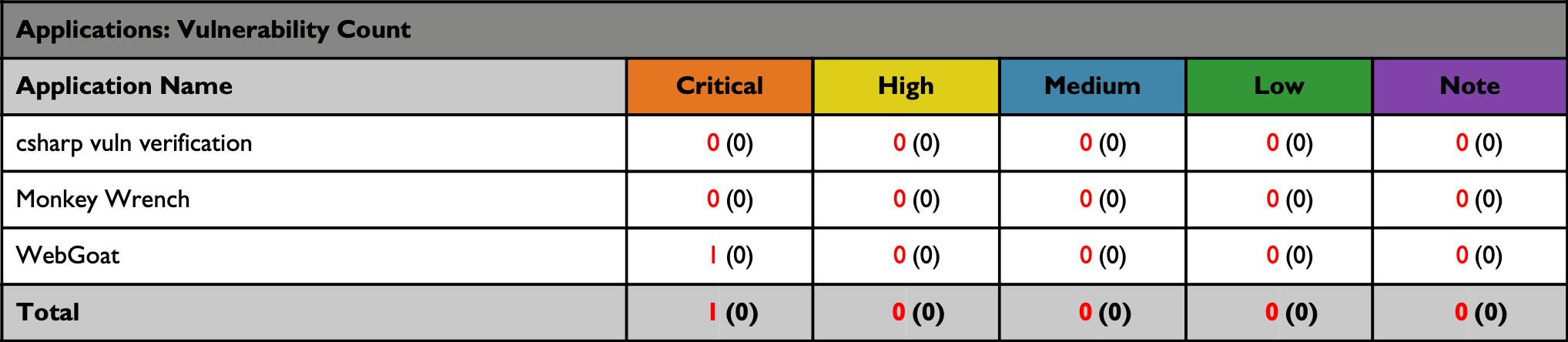
The following table shows the number of vulnerabilities for each application, broken down by rating type.
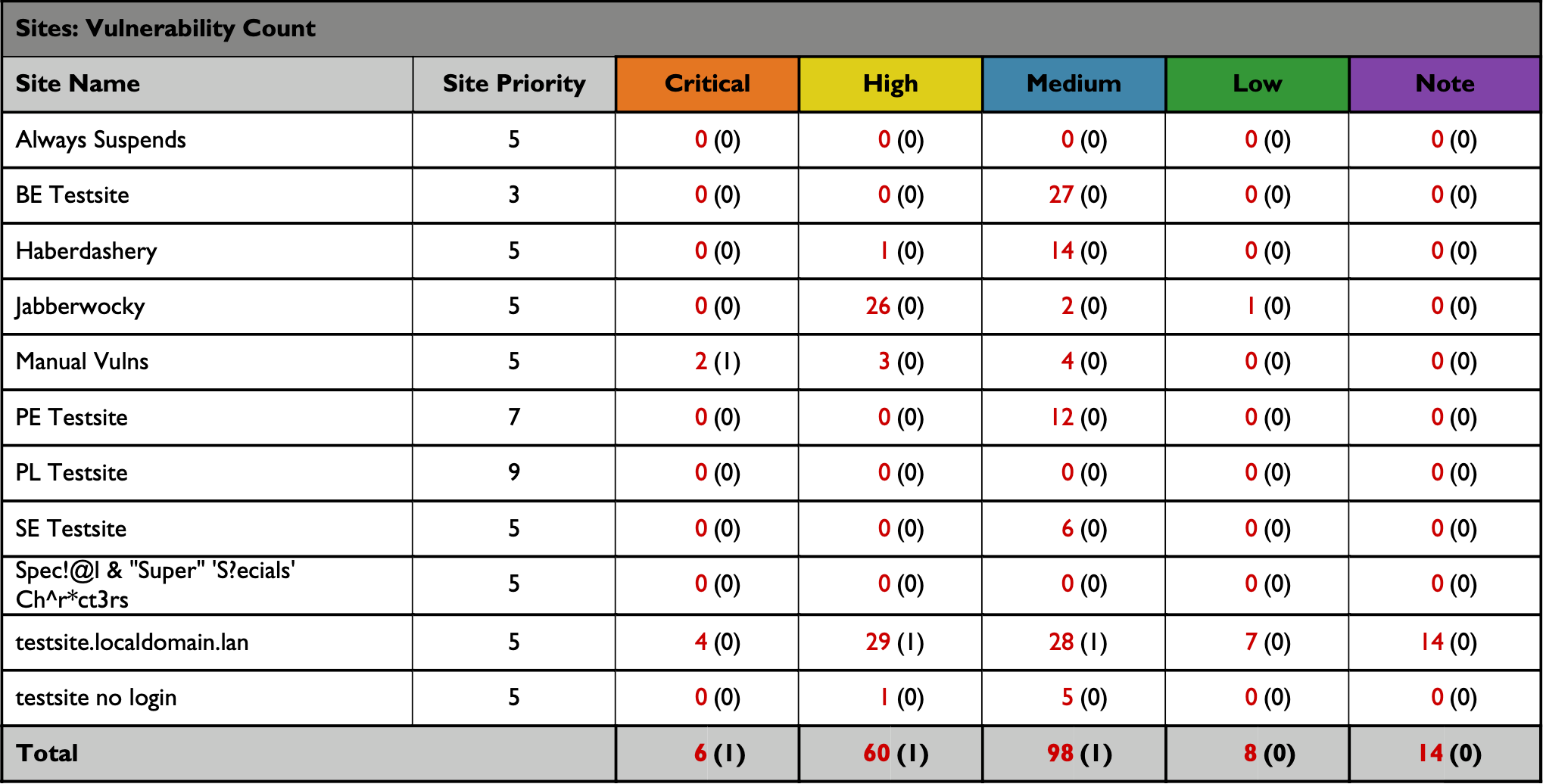
The following table displays a summary of vulnerabilities found across your sites, grouped by their vulnerability classes. The vulnerabilities are sorted by alphabetical order on vulnerability class name.
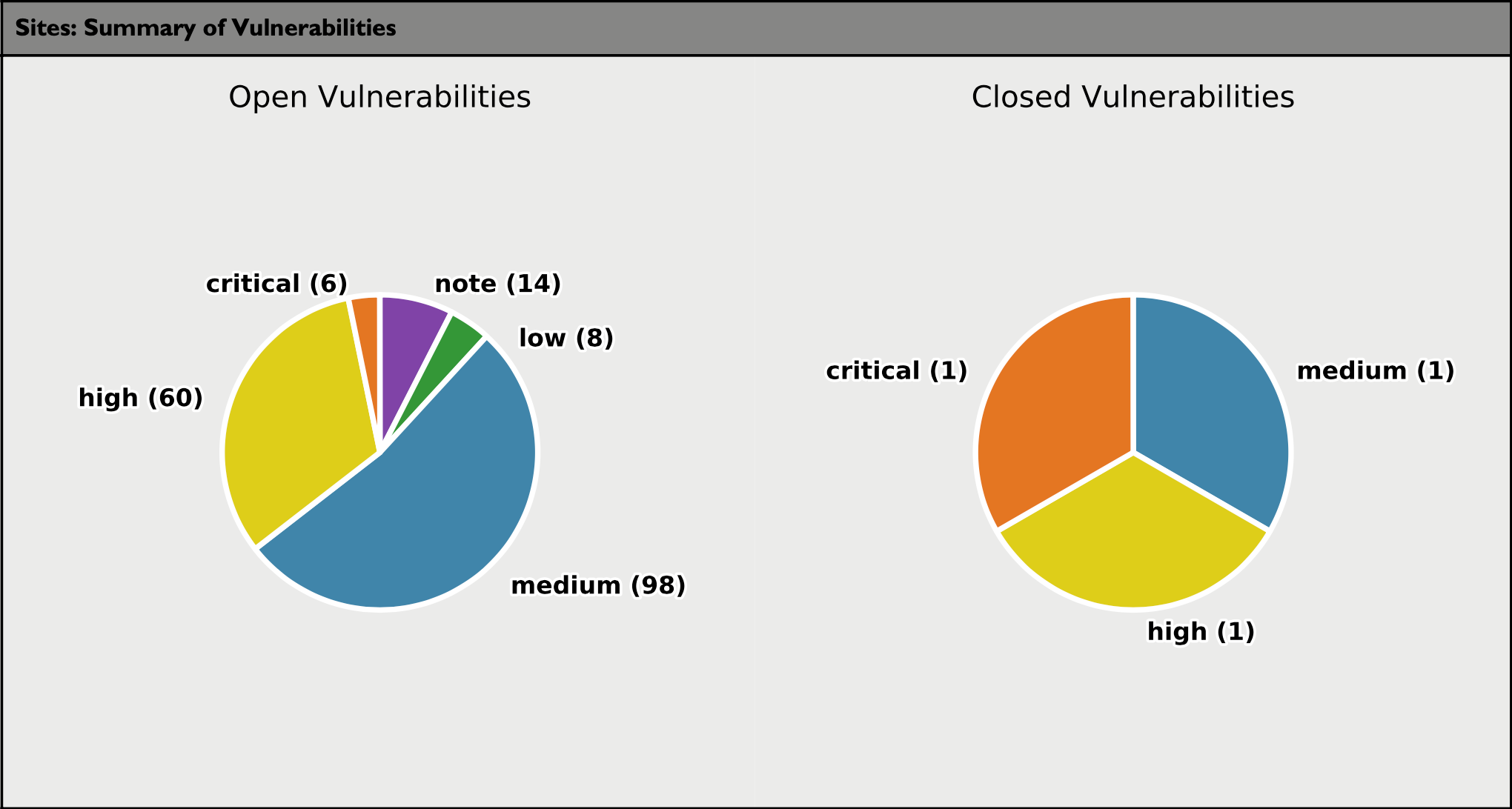
Summary of Vulnerabilities
The following pie chart summarizes your sites' vulnerabilities and includes the vulnerability count for each vulnerability level.
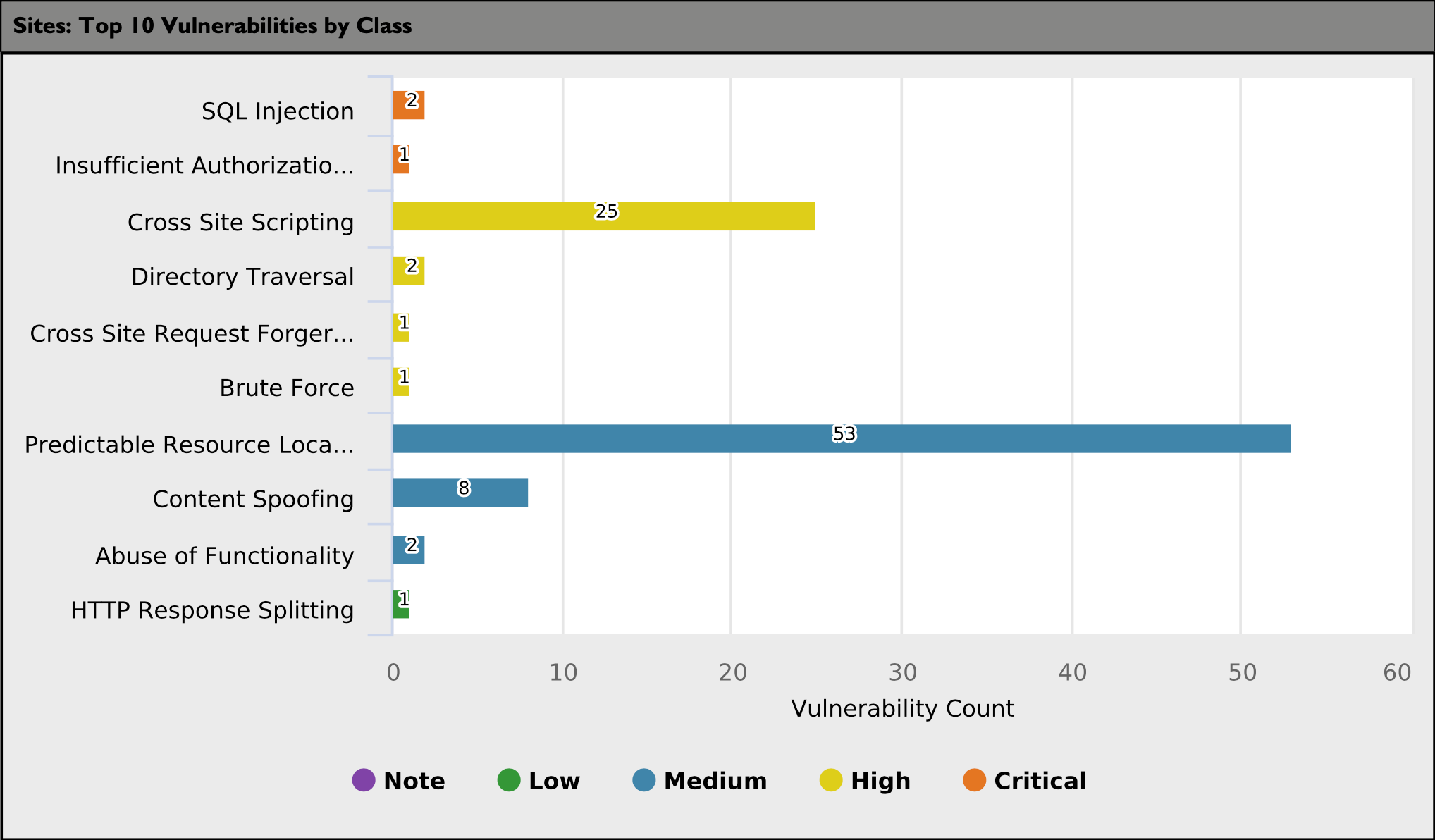
Top 10 Vulnerabilities by Class
The following graph displays the top 10 open vulnerabilities by class and includes the vulnerability count for each class.
Appendix - Vulnerability Level Definitions (by Risk)
This section details how the vulnerability levels are defined, risk Levels for the Sentinel Source solution are based on the OWASP risk rating methodology, based on the standard risk model (Risk = Likelihood x Impact) with several factors contributing to the likelihood and impact. The following tables show how the vulnerability ratings are calculated in The Asset Summary Report.
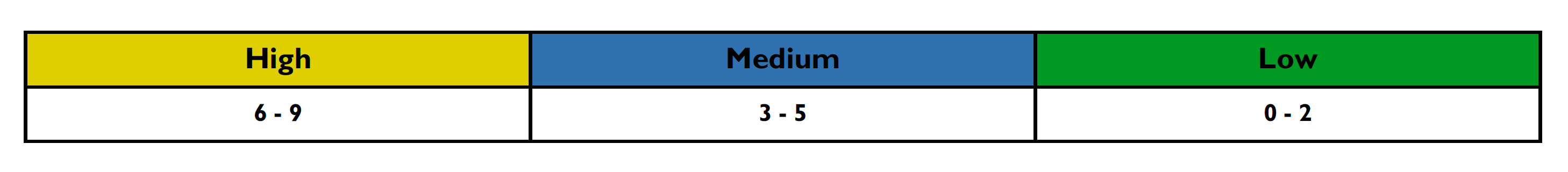
-
The Impact can be broken down into the Technical Impact and Business Impact.
-
Technical impact considers the traditional areas of security: confidentiality, integrity, availability, and accountability.
-
The business impact stems from the technical impact and consider things such as: financial damage, reputational damage, non-compliance, and privacy violations.
-
After scoring the Likelihood and Impact, the Risk Rating is determined using the following table:
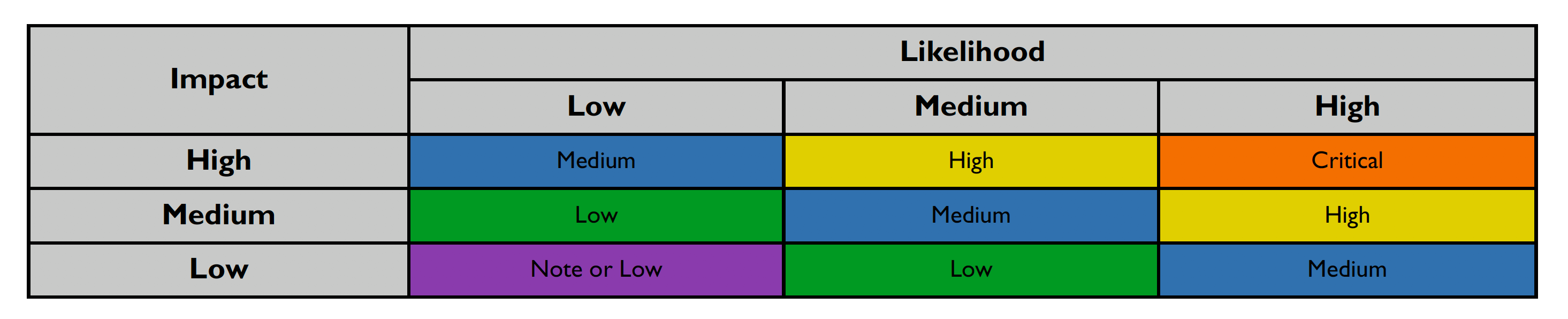
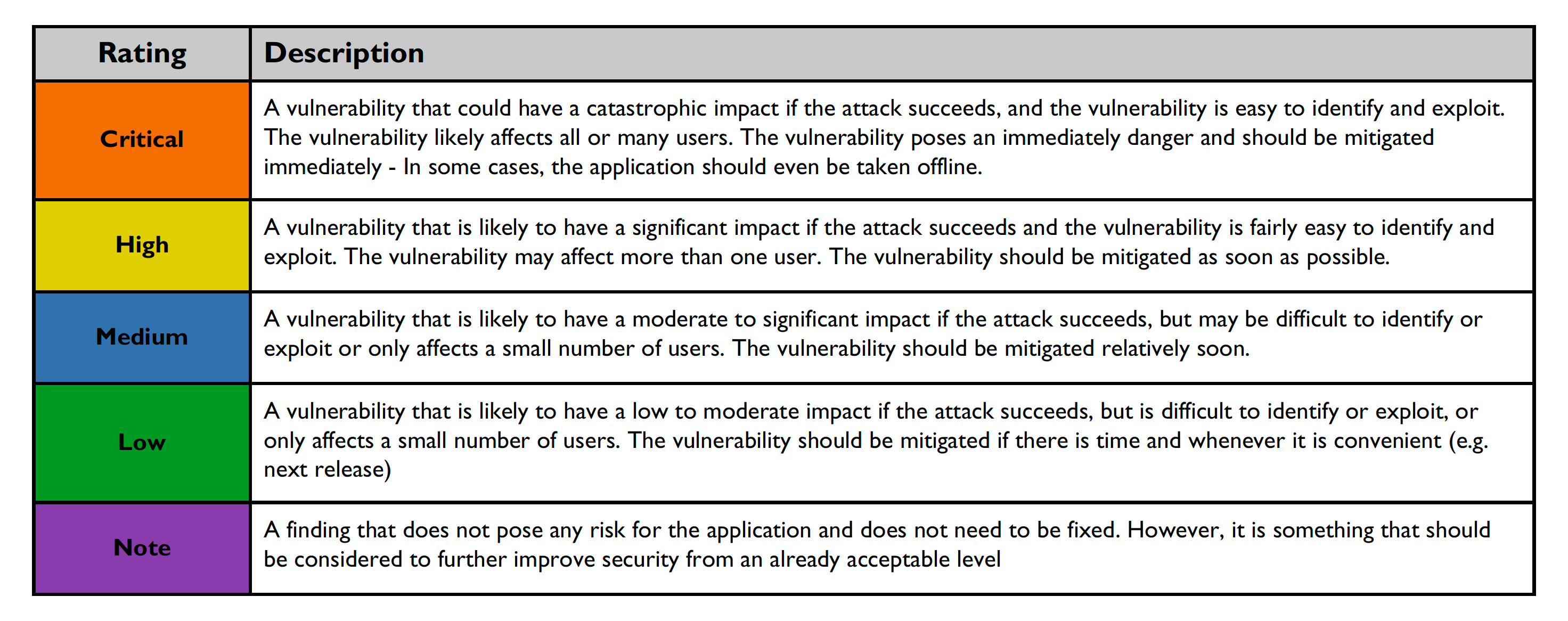
Risk ratings are defined below.
The Asset Summary Report - Options
For the Asset Summary Report, you can choose to see Open, Closed, or Both (all) vulnerabilities for any or all severity level(s). For more information on generating reports, please see Reports Section.