The Vulnerability Detail Screen: Sites
The Site Vulnerability Detail screen, available from the Summary tab, the Assets tab, or the Findings tab, gives you exact details about a specific vulnerability.
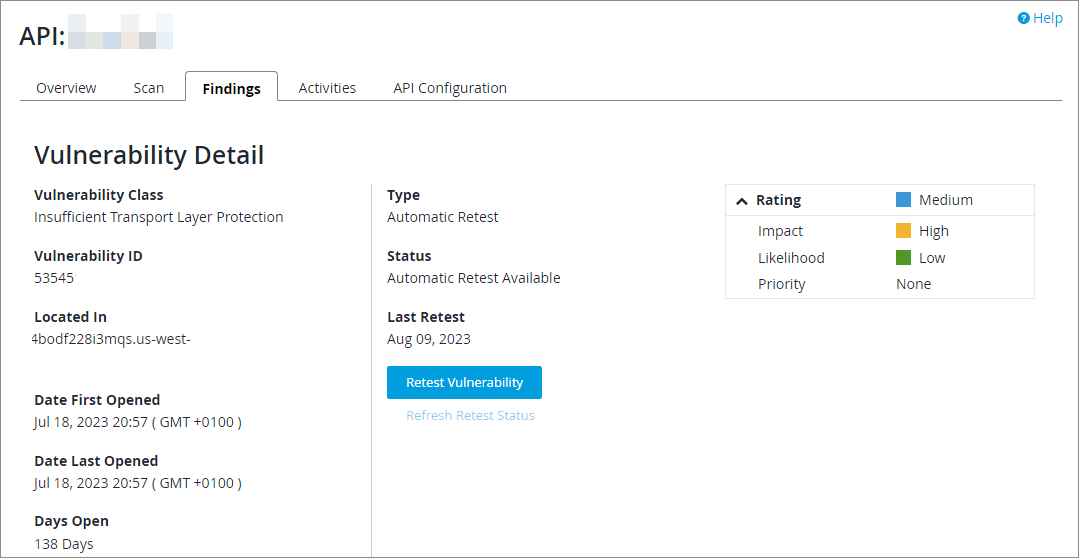
From here you can review the vulnerability information, including the class, location, status, date opened, and CVSS score; you can also request a vulnerability retest with the "Retest Vulnerability" button.
| From the Site Vulnerability Detail screen, you can also go to the Attack Vector Details screen, from which you can add Attack Vector Notes. |
Information available on this screen includes:
-
The Vulnerability Class is the name of the general type of vulnerability — for example, cross-site scripting or sql injection.
-
The Vulnerability ID is the Continuous Dynamic ID for this specific vulnerability.
-
"Located In" gives the path to the vulnerability (the URL for a site or the repository path for an application).
-
"Date Opened" is the date the vulnerability was reported.
-
"Days Open" is the number of days the vulnerability is or was open. The number is rounded down.
-
"Status" is open, closed, accepted, mitigated, or invalid. (Please see "Vuln Status.")
-
The CVSS (Common Vulnerability Scoring System) Score is a numerical representation of the level of likelihood that a vulnerability will (a) be used, and (b) cause damage; a detailed explanation can be found at nvd.nist.gov/cvss.cfm. Note that the Continuous Dynamic Portal’s CVSS scores are based only on the exploitability and impact scores; Black Duck does not have the customer information necessary to determine environmental or temporal scores. In the CVSS system, higher numbers represent greater risk. The vector is a representation of various risk factors explained in detail at nvd.nist.gov/cvss/Vector-v2.aspx.
-
"Rating" is the result of factors including the potential business impact and feasibility of an exploit against the site using this vulnerability, and the priority the customer has set for this site if any.
-
The "Retest Vulnerability" button allows you to request a retest for this vulnerability.
At the bottom of the screen are additional tabs, each of which offers specific information.

The Open Attack Vectors tab lists open vectors, with the vector id, request url, parameter value, and method. Notes can be added by clicking on the plus sign in the notes column.
The Closed Attack Vectors tab lists closed vectors, with the vector id, request url, parameter value, and method. Notes can be added by clicking on the plus sign in the notes column.
The Description *and Solution* tab(s) give a description of the vulnerability, a reference giving more details, a recommended solution, and solution references.
If you need more information about the vulnerability than is available in the Description & Solution tab, you can use the Ask a Question tab for clarification. Questions submitted here are routed directly to our engineers, bypassing the Black Duck Community.
Ask a Question
To ask a question using the Vulnerability Management functions, perform the following steps:
-
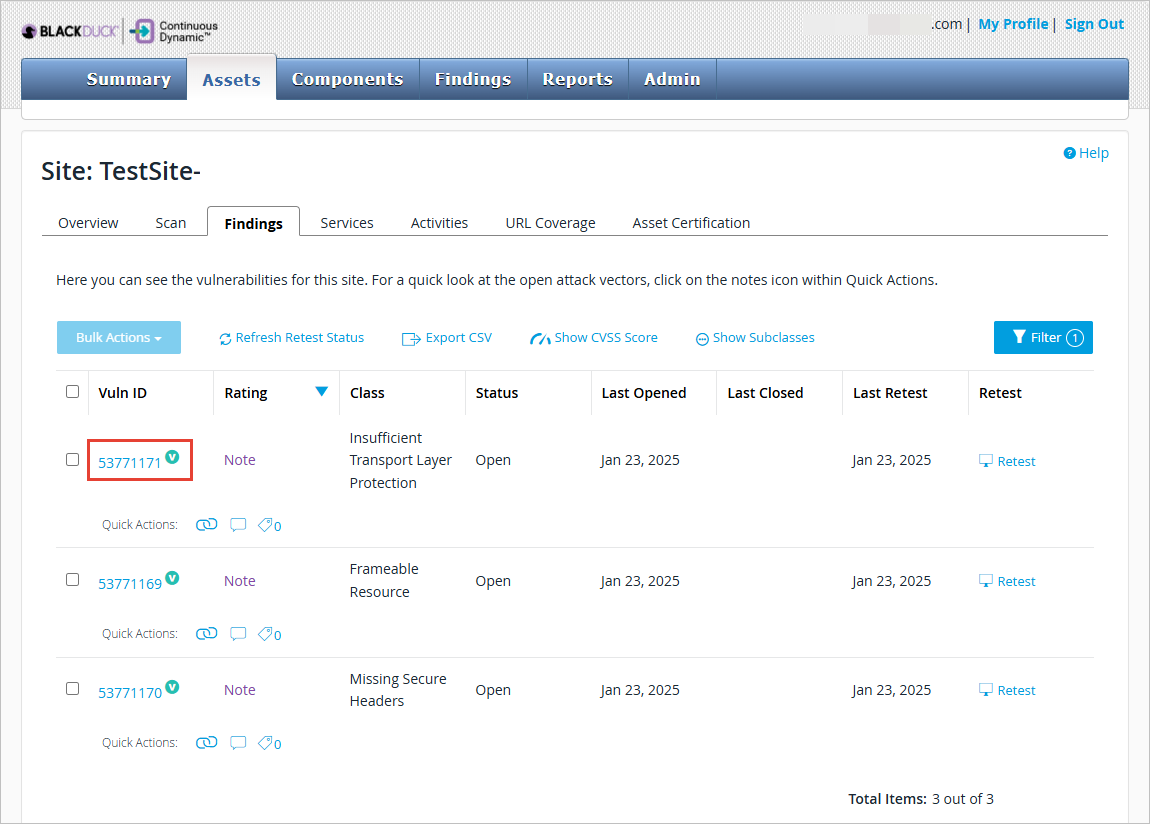
Click Findings.
-
Select a Vuln ID from the Vulnerability Management page.
-
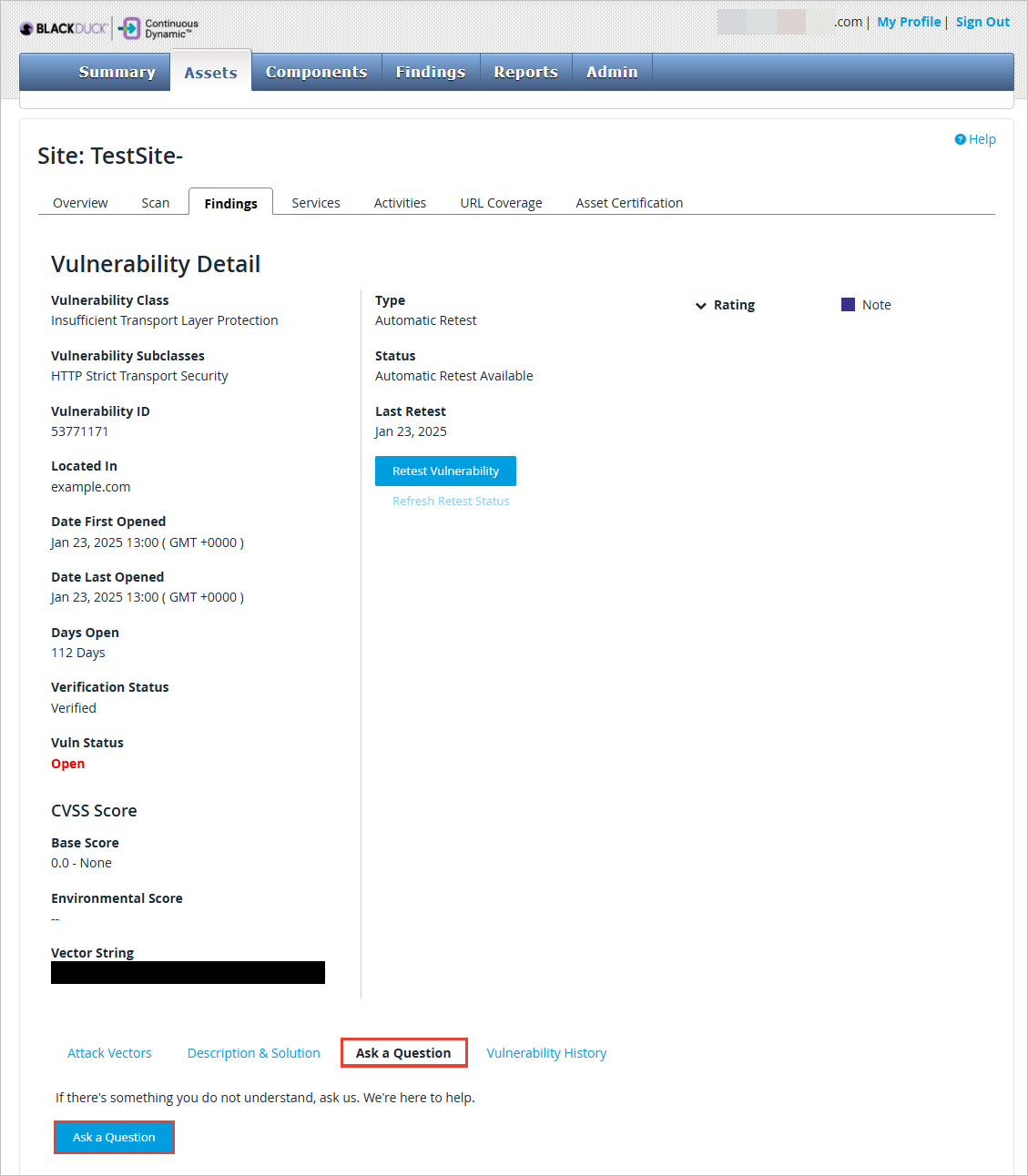
Select Ask a Question.
-
Click the Ask a Question button.
-
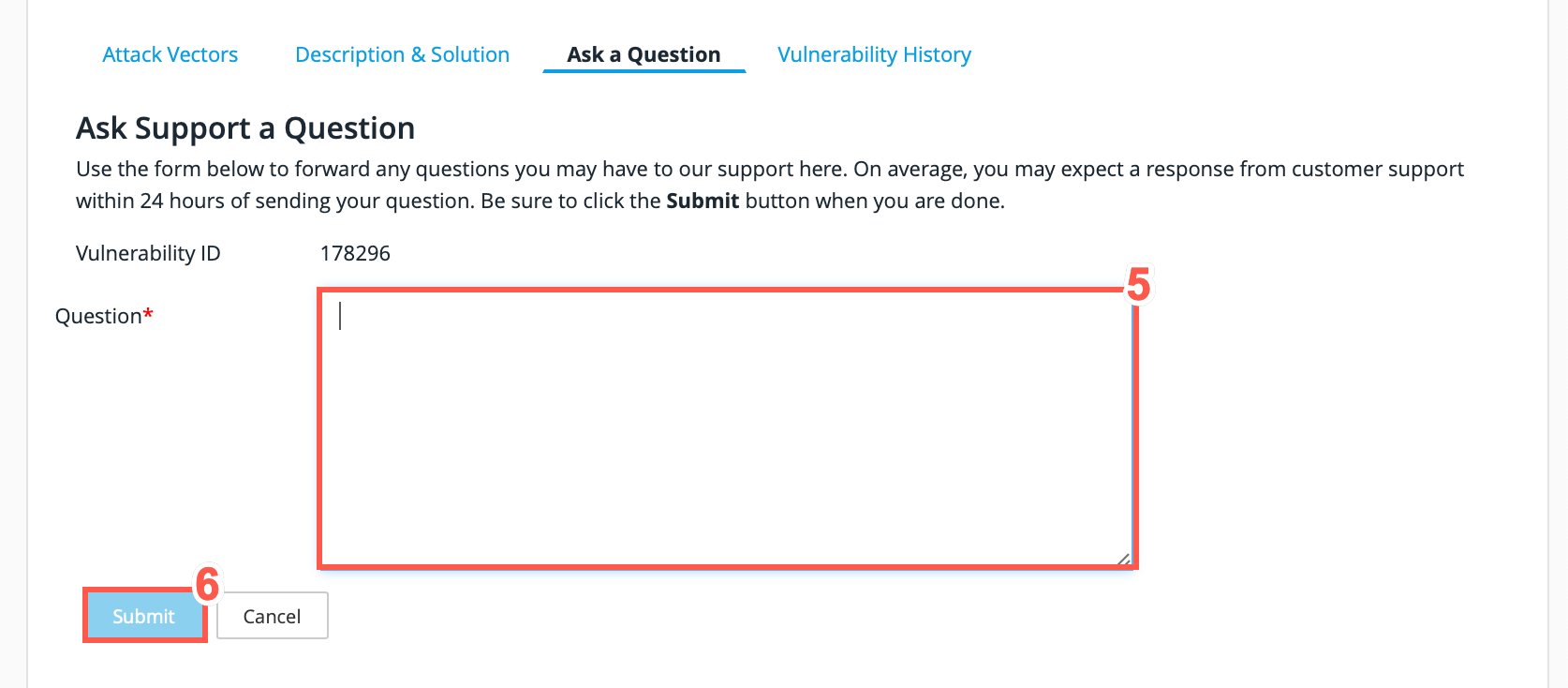
Enter a question in the text field provided.
-
Click Submit to send your question to the Threat Research Center.
| Previous questions and responses can be reviewed in the Ask a Question section. |
The Vulnerability History tab will show you the vulnerability activities for this site for the past 90 days; you can filter the listing to see a shorter time period.
For user guides and additional information, log on to the Black Duck Community.
To provide feedback on the user documentation, please email continuousdynamicdocs@blackduck.com. Thank you!