Security Audit Report
The Security Audit Report provides an overview of open vulnerabilities discovered in the assessment, including summaries, metrics, and conclusions. For those customers using both Continuous Dynamic and Sentinel Source, this report will cover both dynamic and static test results.
| You can choose whether to include or refrain from including a count of the vulnerabilities. |
Vulnerability Count
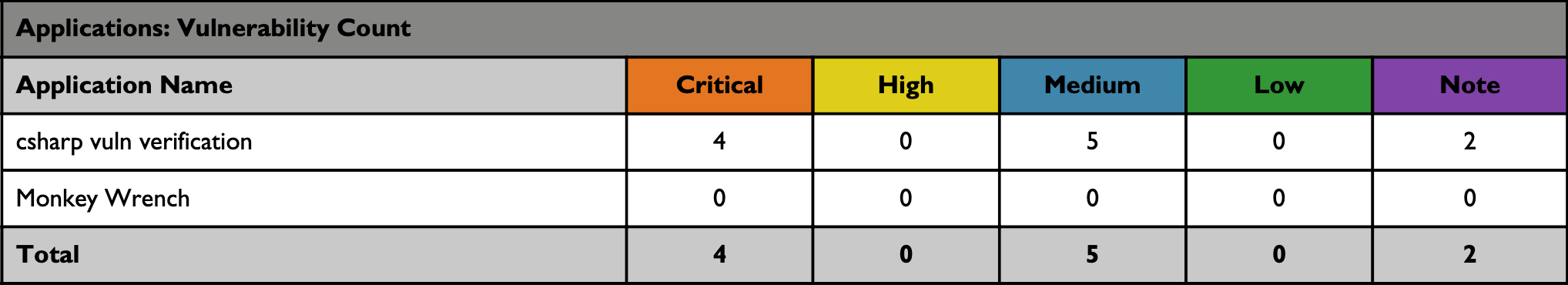
The following table shows the number of vulnerabilities for each site or application, broken down by rating type.
Open Vulnerabilities Categories
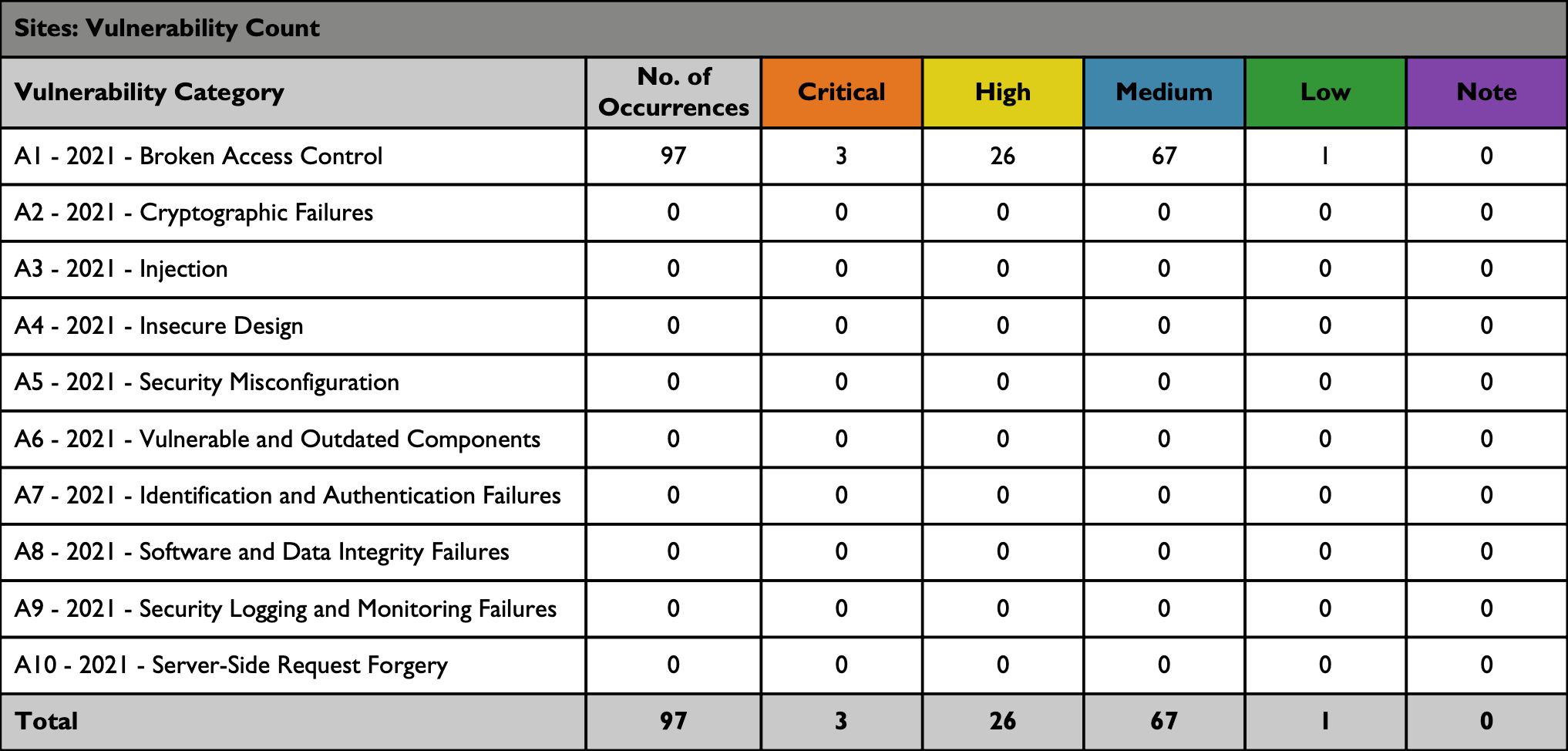
The following table summarizes the vulnerabilities found by Black Duck that also fall into the OWASP Top 10 Categories. Not all Continuous Dynamic vulnerability classes are represented in the OWASP Top 10 Categories, so not all identified on your assets may be accounted for in this table.
Summary of Vulnerabilities
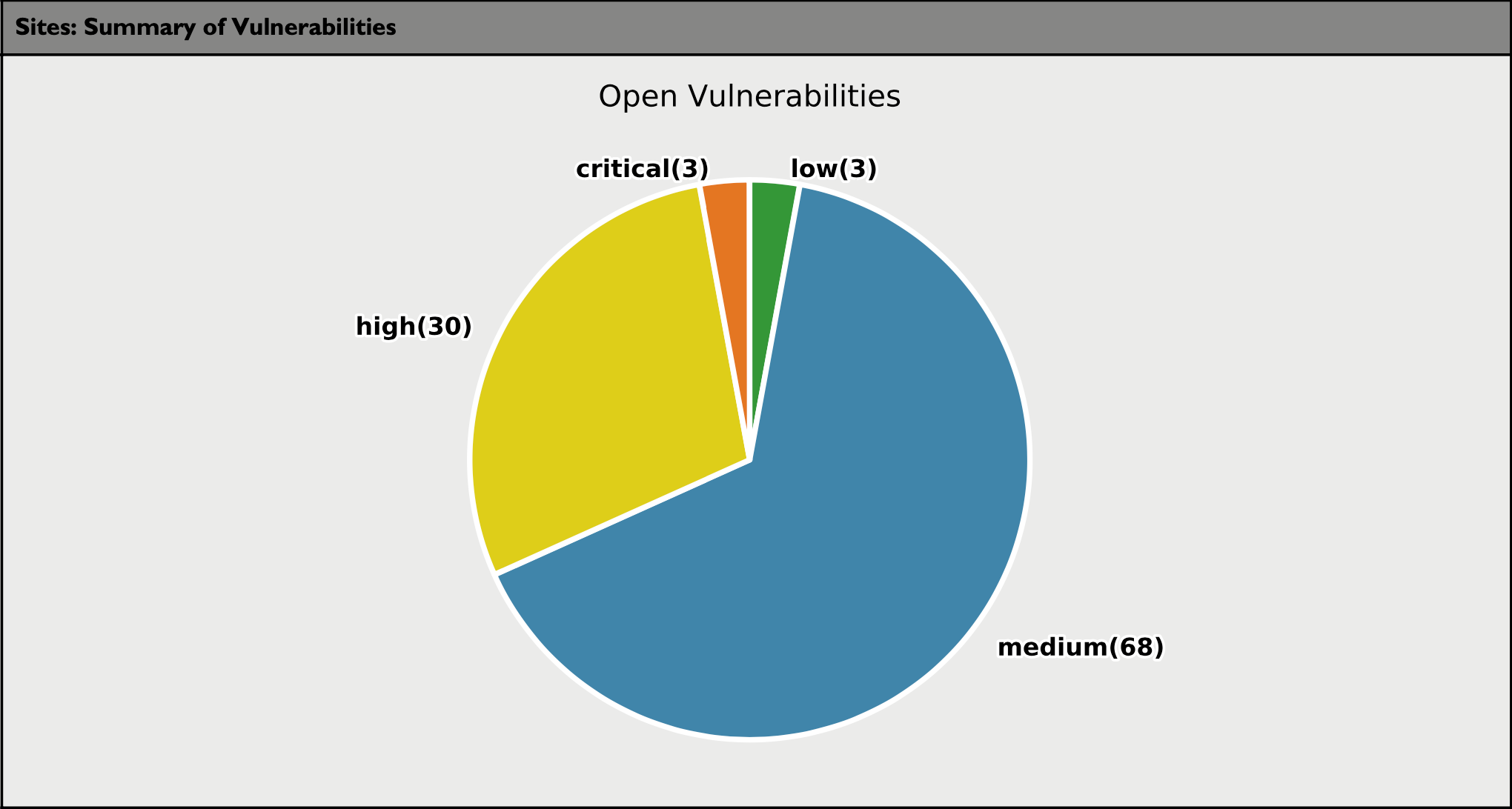
The following pie chart summarizes the open vulnerabilities and includes the vulnerability count.
Continuous Dynamic Premium Edition
Continuous Dynamic Premium Edition service level tests for the following list of WASC classes of Web vulnerabilities:
Authentication Tests
-
Brute Force
-
Insufficient Authentication
-
Weak Password Recovery
-
Cross-site Request Forgery
-
Credential/Session Prediction
-
Insufficient Authorization
-
Insufficient Session Expiration
-
Session Fixation
Client-side Attack Tests
-
Content Spoofing
-
Cross-site Scripting
-
HTTP Response Splitting
Command Execution Tests
-
Buffer Overflow
-
Format String Attack
-
LDAP Injection
-
OS Commanding
-
SQL Injection
-
SSI Injection
-
XPath Injection
Information Disclosure Tests
-
Directory Indexing
-
Information Leakage
-
Path Traversal
-
Predictable Resource Location
Logical Attack Tests
-
Abuse of Functionality
-
Denial of Service
-
Insufficient Anti-automation
-
Insufficient Process validation
Appendix - Vulnerability Level Definitions (by Risk)
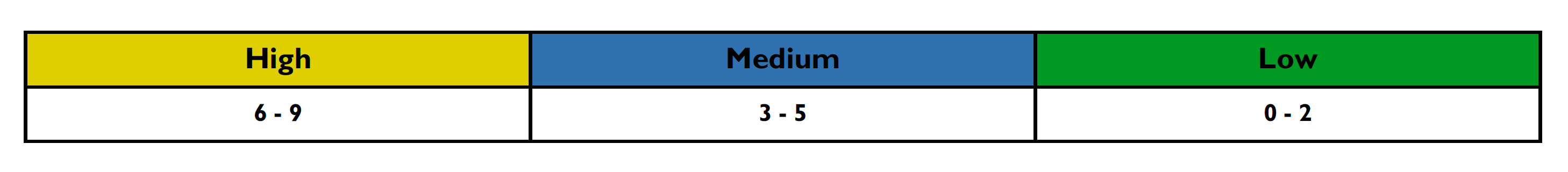
This section details how the vulnerability levels are defined, risk Levels for the Sentinel Source solution are based on the OWASP risk rating methodology, based on the standard risk model (Risk = Likelihood x Impact) with several factors contributing to the likelihood and impact. The following tables show how the vulnerability ratings are calculated in The Security Audit Report.
-
The Impact can be broken down into the Technical Impact and Business Impact.
-
Technical impact considers the traditional areas of security: confidentiality, integrity, availability, and accountability.
-
The business impact stems from the technical impact and consider things such as: financial damage, reputational damage, non-compliance, and privacy violations.
-
After scoring the Likelihood and Impact, the Risk Rating is determined using the following table:
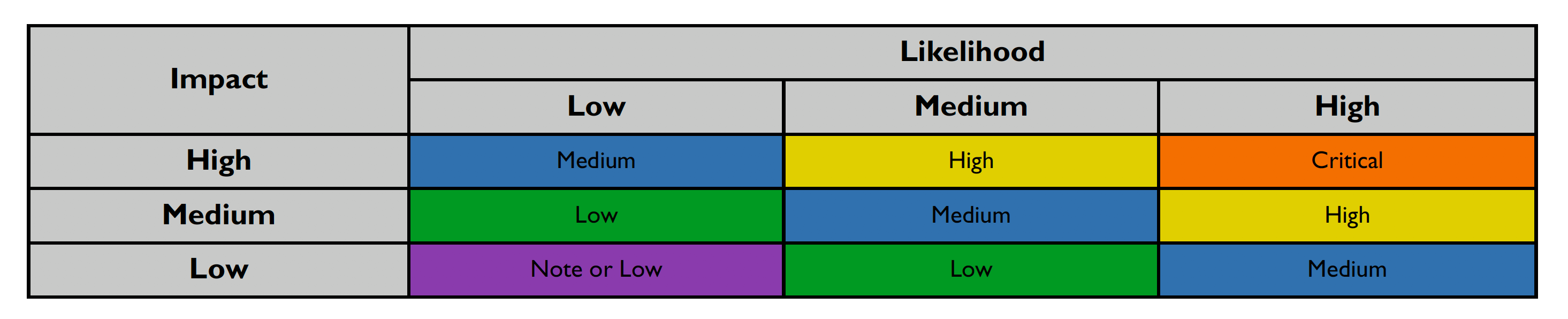
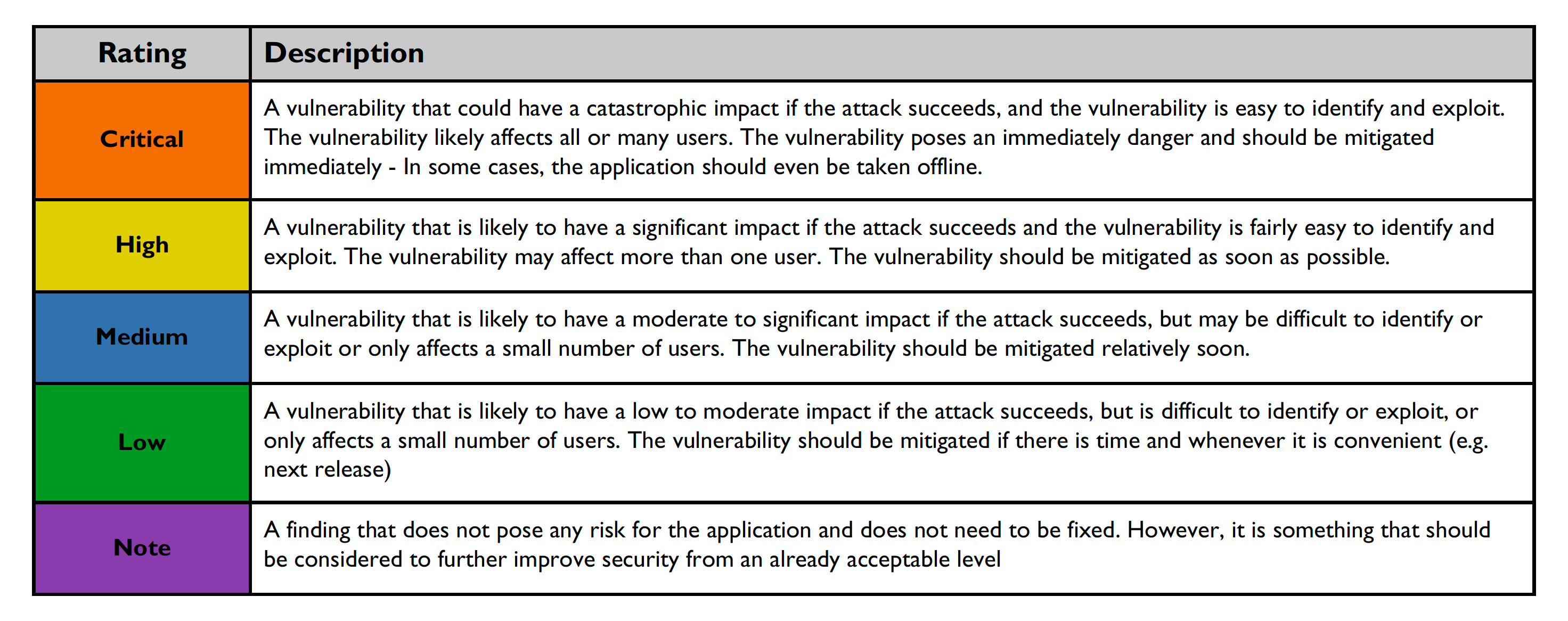
Risk ratings are defined below:
For more information on generating reports, please see Report Section.