PCI 3.2 Compliance Report
The PCI 3.2 Compliance report documents compliance with the Payment Card Industry’s Data Security Standard (PCI-DSS Version 3.2), which includes requirements that web applications be built to secure coding guidelines and that applications be subject to routine vulnerability checks.
List of Sites
The PCI 3.2 Compliance Report provides a list of sites included in this report, shown below.
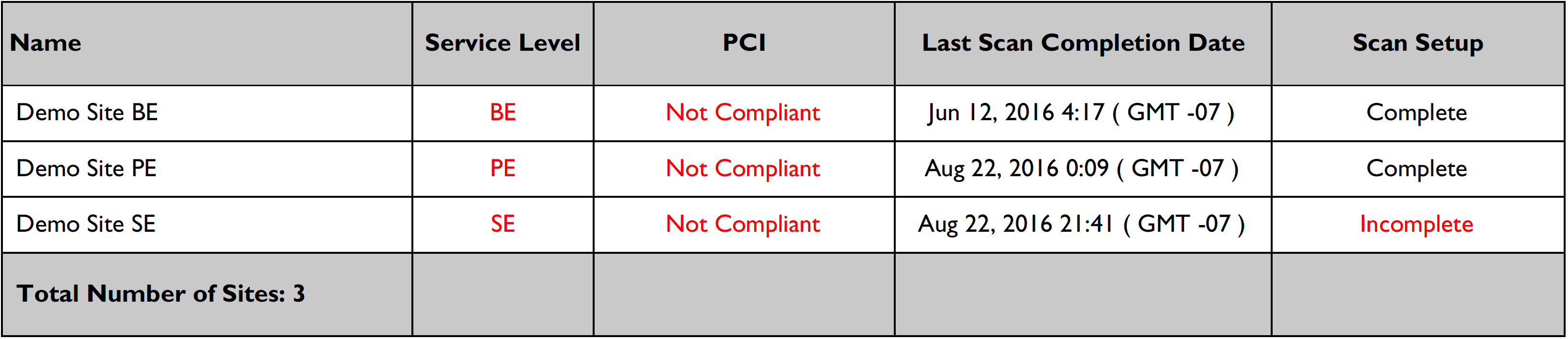
| Sites are marked as compliant or not compliant based on passing or not passing the tests that are performed at that service level. True PCI compliance is dependent on all tests being performed. Sites at the BE or SE service levels cannot be described as fully PCI compliant based on the BE or SE testing. However, they will be described as compliant in this table if the tests performed passed. |
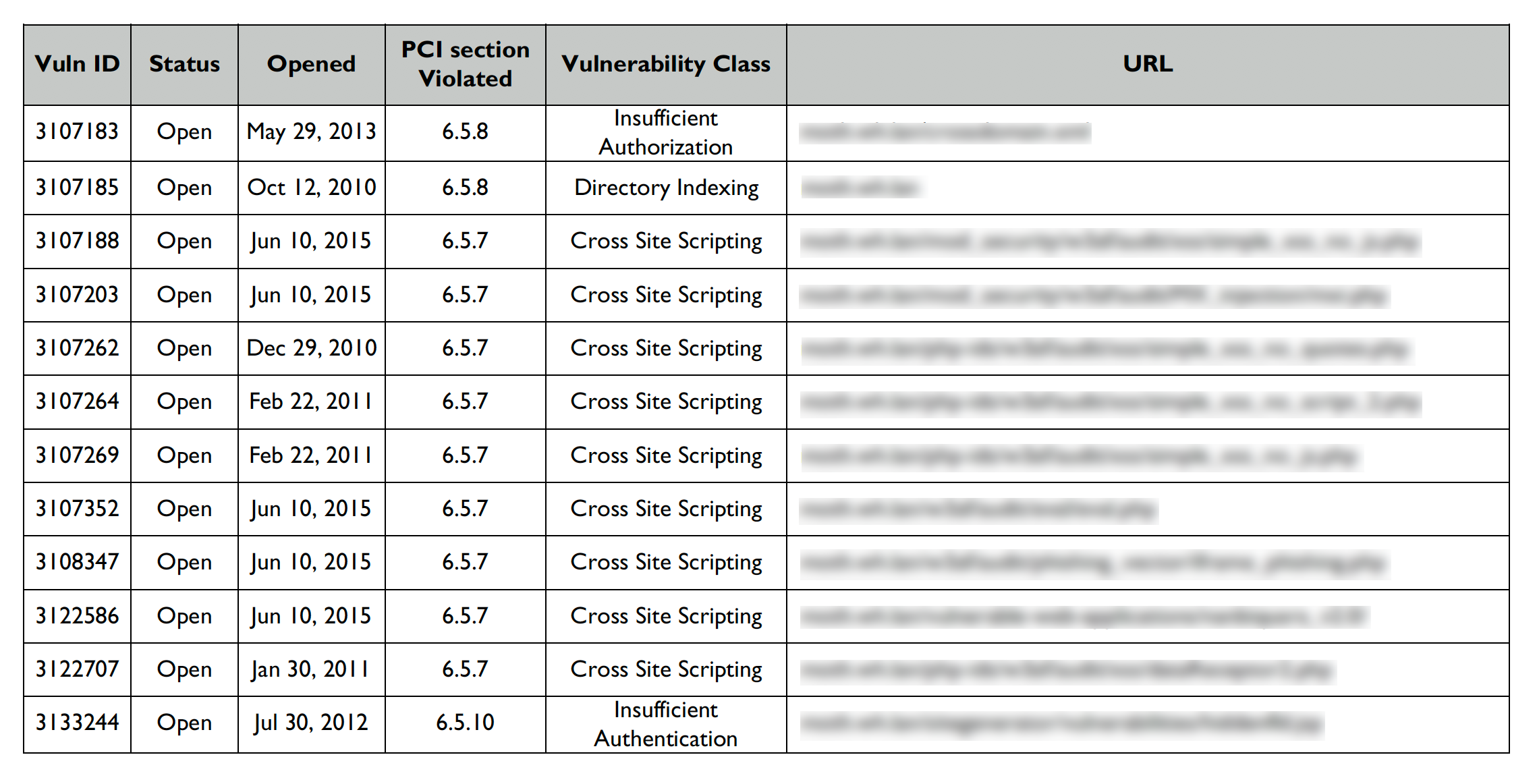
PCI Compliance Summary
This table lists the requirements specified by the PCI-DSS for Web applications, and whether your site complies with each requirement (6.5.1 - 6.5.10).
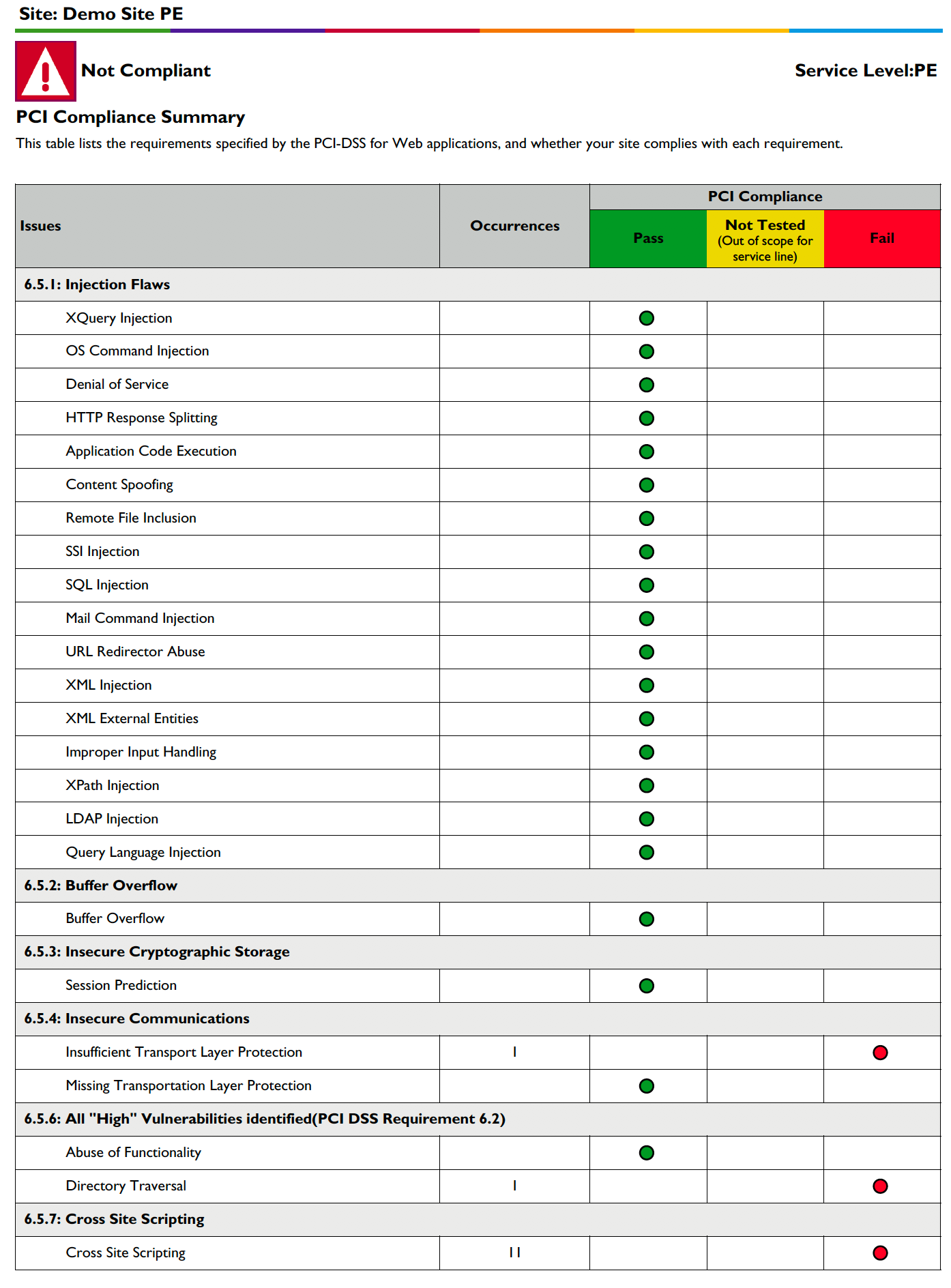
| This report is extremely useful for those cases when it is necessary for you to demonstrate that a site is PCI-compliant. |
Appendix PCI-DSS Requirements
The PCI 3.2 Compliance report documents compliance with the latest PCI-DSS (3.2) requirements as follows:
-
6.5.1: Injection Flaws
-
6.5.2: Buffer Overflow
-
6.5.3: Insecure Cryptographic Storage
-
6.5.4: Insecure Communications
-
6.5.5: Improper Error Handling
-
6.5.6: All 'High' Vulnerabilities identified (PCI-DSS Requirement 6.2)
-
6.5.7: Cross Site Scripting
-
6.5.8: Improper Access Control
-
6.5.9: Cross Site Request Forgery
-
6.5.10: Broken Authentication and Session Management
The report contains appendix pages for each requirement, these appendix pages include,
-
Environments Affected
-
Vulnerability
-
Verifying Security
-
Protection
-
Samples
-
Related Articles
-
How to Protect Yourself
-
References
Appendix - Vulnerability Level Definitions (by Risk)
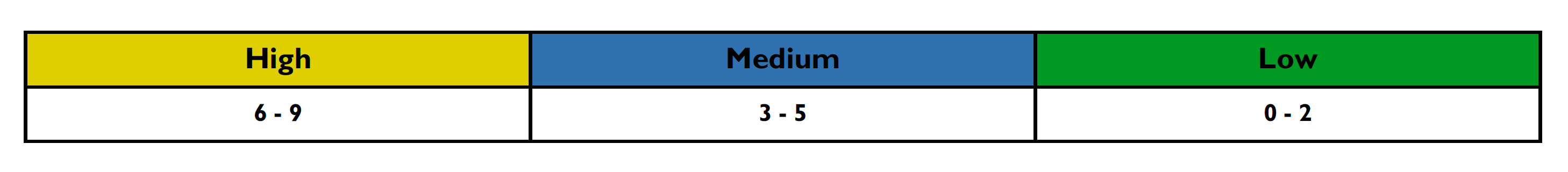
This section details how the vulnerability levels are defined. Risk Levels for the Sentinel Source solution are based on the OWASP risk rating methodology, based on the standard risk model (Risk = Likelihood x Impact) with several factors contributing to the likelihood and impact. The following tables show how the vulnerability ratings are calculated in The PCI 3.2 Compliance Report.
The Impact can be broken down into the Technical Impact and Business Impact.
-
Technical impact considers the traditional areas of security: confidentiality, integrity, availability, and accountability.
-
The business impact stems from the technical impact and considers things such as: financial damage, reputational damage, non-compliance, and privacy violations.
After scoring the Likelihood and Impact, the Risk Rating is determined using the following table:
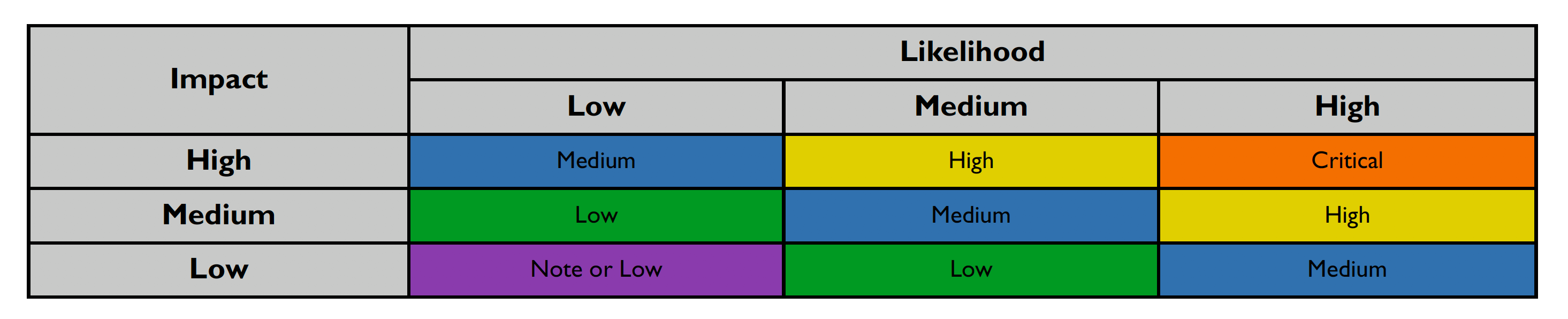
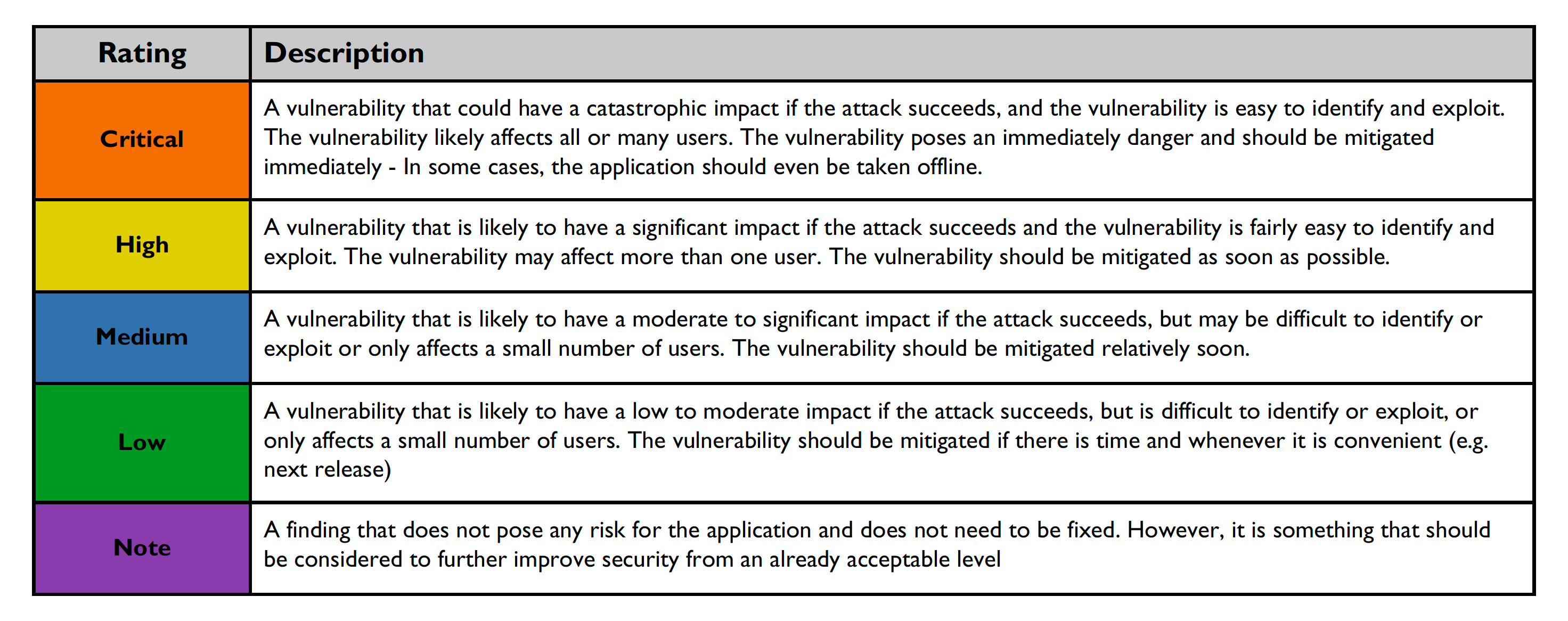
Risk ratings are defined below:
For more information on generating reports, please see The Continuous Dynamic Portal Menu - Reports.