PAM Authentication Overview
| The Account Overview tab is only available to users with Admin permissions associated with their account. |
About the HashiCorp® PAM Integration
Continuous Dynamic offers a native integration with Privileged Access Management (PAM) solutions from HashiCorp®. This gives you additional flexibility over where to store scanning credentials for sites that require user authentication.
If you decide to use the PAM integration, you will store and manage your site scanning credentials in HashiCorp Vault instead of the Continuous Dynamic Portal. Vault is a system that provides centralized privileged access and secrets management for enterprises. When setting up the integration, you can choose whether to authenticate with Vault directly or to broker credentials through HashiCorp Boundary, a proxy for secure access management.
When adding a Site asset, Portal users can select a "PAM credentials object" instead of entering username and password credentials. When a site scan is initiated, Continuous Dynamic authenticates to Vault, obtains a unique ID for the configured Vault asset, retrieves the scanning credentials, and then initiates the scan. If credentials have changed in Vault, Continuous Dynamic updates the customized login sequence automatically, avoiding interruptions in scanning.
PAM credentials can also be used for Business Logic Assessments.
| To use the PAM integration, your scanning credentials must be stored in HashiCorp Vault. Other PAM providers and platforms are not supported. PAM integration is not supported for API assets added using AutoAPI. |
Benefits of using a PAM
Managing site scanning credentials in a PAM solution is both secure and efficient.
-
Store credentials centrally with other secrets.
-
Secure and automated retrieval of credentials. Removes the need to log into the Portal and update credentials every time they change or are rotated.
-
Automatically enforce company security policies, such as password rotation and expiry.
-
Meet enterprise compliance and security demands.
Prerequisites
-
The latest version of HashiCorp HCP Vault Dedicated (cloud hosted) or Vault Enterprise (self-managed).
-
Scanning credentials for Site assets in Continuous Dynamic are stored in Vault.
-
You have configured a supported authentication method in HashiCorp; see "Supported Authentication Methods", below.
-
An HCP Boundary installation is required to use the Token and Credentials authentication methods.
Supported Authentication Methods
The integration supports three authentication methods for Continuous Dynamic to integrate with Vault and retrieve site scanning credentials. These are described in the following table:
| Authentication method | Platform | Description and setup |
|---|---|---|
Token: Brokered credentials, API key |
HashiCorp Boundary |
Authenticate to Vault through HashiCorp Boundary with the use of "brokered credentials", via your API key. To use this method, provide your Boundary API token (key) in the Continuous Dynamic Portal. You can find your API key in the HashiCorp Cloud Portal. By default, the time to live (TTL) for a Boundary API token is 7 days. When creating your API token for Boundary, consider increasing the default TTL to a duration that meets your security requirements. See https://developer.hashicorp.com/hcp/docs/boundary/configure-ttl for further details. |
Credentials: Brokered credentials, username and password |
HashiCorp Boundary |
Authenticate to Vault through HashiCorp Boundary with the use of "brokered credentials", via a username and password. To use this method, provide a set of Boundary credentials (username and password) and an By default, the TTL for a Boundary API token is 7 days. When creating your API token for Boundary, consider increasing the default TTL to a duration that meets your security requirements. See https://developer.hashicorp.com/hcp/docs/boundary/configure-ttl for further details. |
App Role credentials |
HashiCorp Vault |
Authenticate directly to Vault by using the AppRole auth method (see Use AppRole Authentication in the Vault documentation). Note that KV secrets engine version 1 or 2 is required. To use this method, provide your You must have added Continuous Dynamic IP Address ranges to your allow list. |
Creating a PAM Credentials Object
Create a PAM credentials object configured to connect to Vault using a specified authentication type.
-
Log in to the Continuous Dynamic Portal as a user with Admin permissions.
-
Select Admin > Account Overview.
-
Select the PAM Authentication subtab.
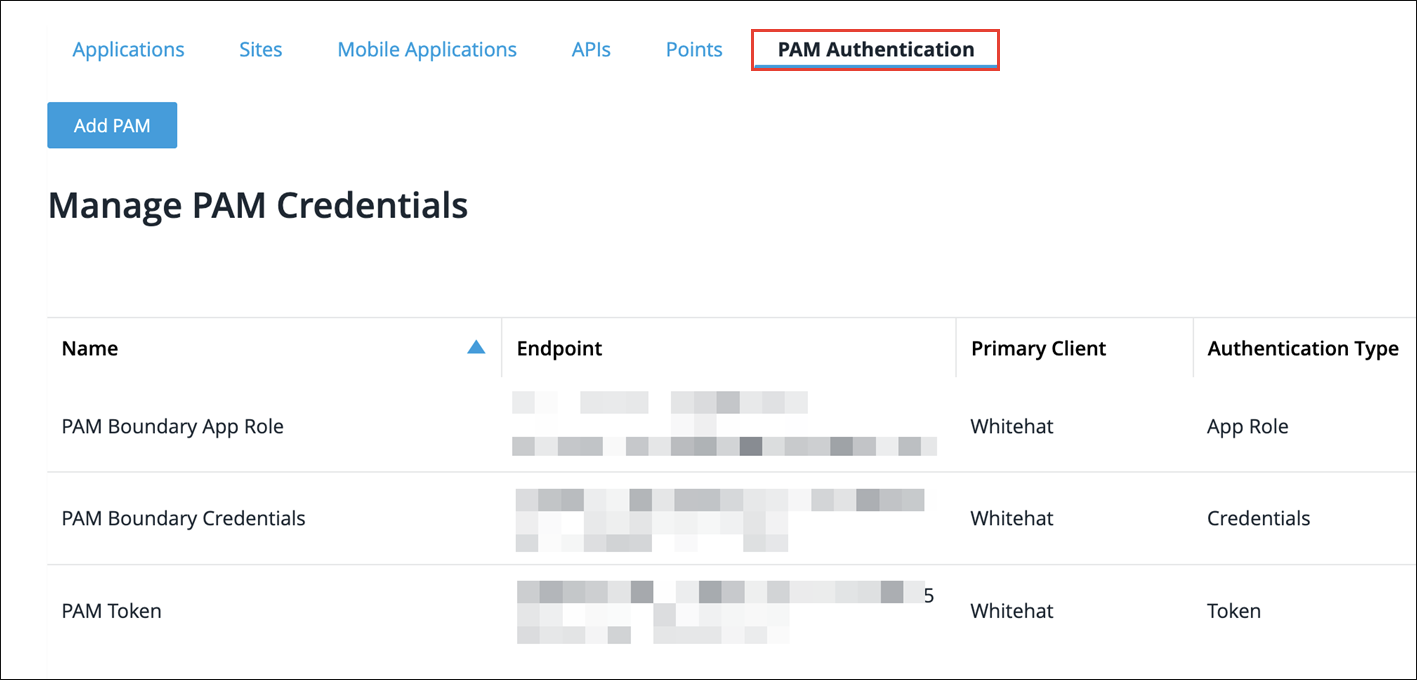
The Manage PAM Credentials page lists all PAM credentials objects in your Client. The table displays the Name, Endpoint, Primary Client, and Authentication Type of each object, as well as the supported Actions.
-
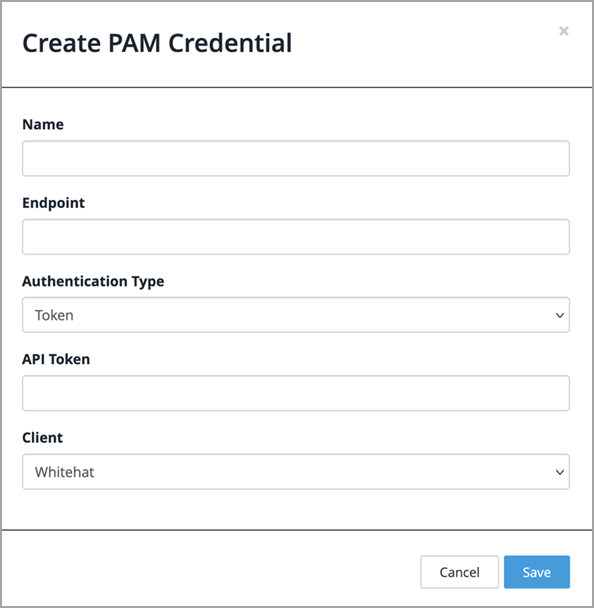
Click Add PAM. The Create PAM Credential dialog is displayed:
-
Enter a Name for the PAM credentials object. This must be unique within your Client.
-
In the Endpoint field, specify the API endpoint of your Vault instance; for example, https://pam.example.com/api. This must be a valid URL.
-
Select a supported Authentication Type:
-
Token - see step 8.
-
Credentials - see step 9.
-
App Role - see step 10.
-
-
To use Token authentication, enter your Boundary API key in the API Token field.
-
To use Credentials authentication, enter the following information:
-
A Username and Password for a user account in Boundary. These credentials must correspond to the Auth Method ID that you specify in the next step.
-
In the Auth Method ID field, enter the Boundary auth method ID, e.g.
ampw_xxP3UIBn2k. Note that the integration supports thepasswordauth method only; see authenticate in the Boundary documentation.
-
-
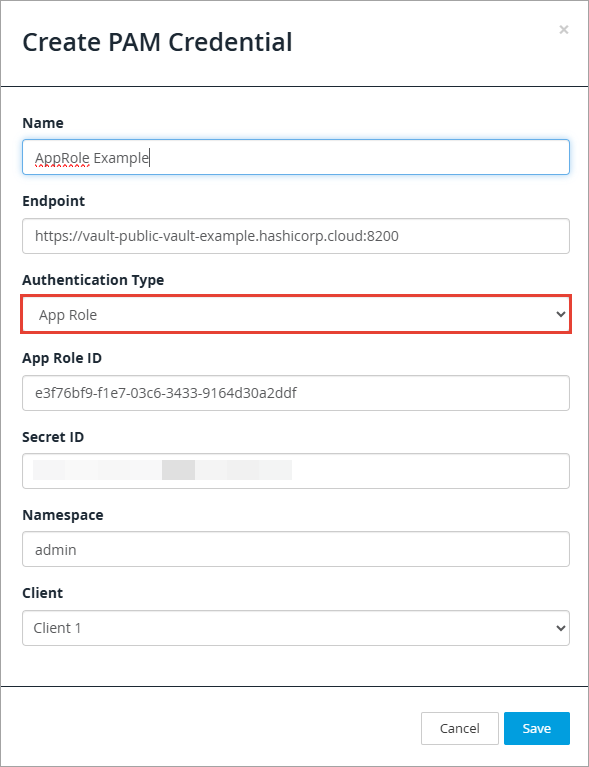
To use AppRole authentication, enter the following information:
-
App Role ID: The
RoleIDof theAppRolein Vault to be used for authentication by Continuous Dynamic. Enter therole_idvalue. -
Secret ID: A
SecretIDis a token that is used with aRoleIDto authenticate to Vault for a specified time to live (TTL). Enter thesecret_idvalue. -
Namespace: The namespace is the Vault secrets engine that contains the target path.
-
-
Select the Continuous Dynamic Client that you want to create the PAM credentials object in (applies to Multi-Client services only).
-
Click Save.
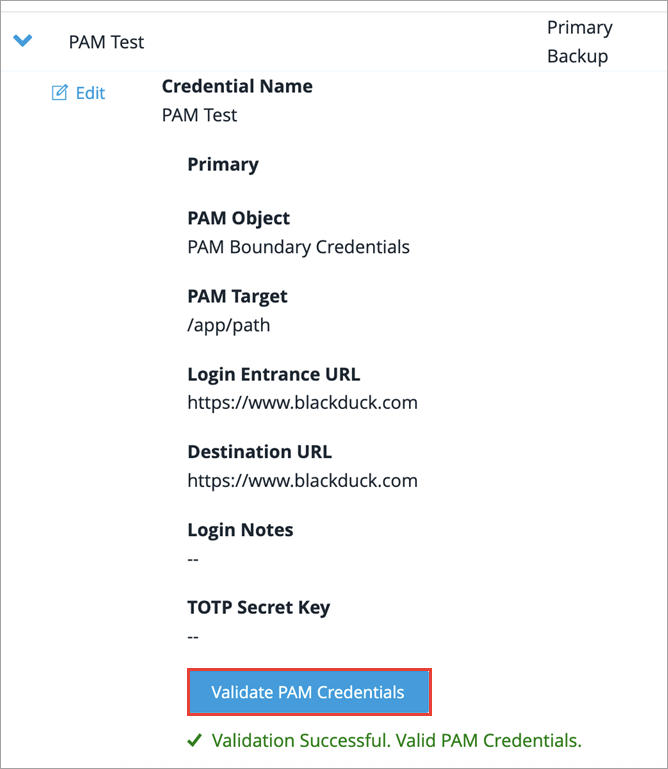
The system checks the validity of the PAM credentials object in real time. If the configuration is valid, a success banner is displayed and the PAM credentials object is saved. If not, an error message gives details of the issues found (for example, the Vault endpoint or Boundary credentials are invalid, or the target is unreachable). You need to resolve these issues before you can save the PAM credentials object.
If successfully saved, the PAM credentials object is now available to users when adding scanning credentials and adding a Site asset.
Managing PAM Credentials Objects
You can edit and delete PAM credentials objects in the PAM Authentication tab.
-
Click Edit, update the information you want to change, then click Save.
-
To delete a PAM credentials object, click Delete.
| You can only delete PAM credentials objects that are not currently in use by Site assets or Business Logic Assessments. |
Validating PAM Credentials Objects
After creating a PAM credentials object, you can periodically check if the configuration is still valid.
-
Navigate to the site Scan tab for an asset to which PAM credentials have been added.
-
In the Credentials for Scanning section, click the blue arrow to expand the PAM credentials.
-
Click Validate PAM Credentials.
The system checks the validity of the PAM credentials object in real time. A success message is displayed if the configuration is still valid.