About the Sentinel Appliance
The Sentinel Appliance is a virtual machine (VM) that enables scanning of internal websites (not accessible via the public Internet) for Continuous Dynamic and source code or binaries for Sentinel Source (SAST).
The Sentinel Appliance enables the Sentinel Service to securely assess applications (with Continuous Dynamic) and source code (with Sentinel Source) in development or in production with the same rigorous and continuous methodology of scanning, verification and custom testing.
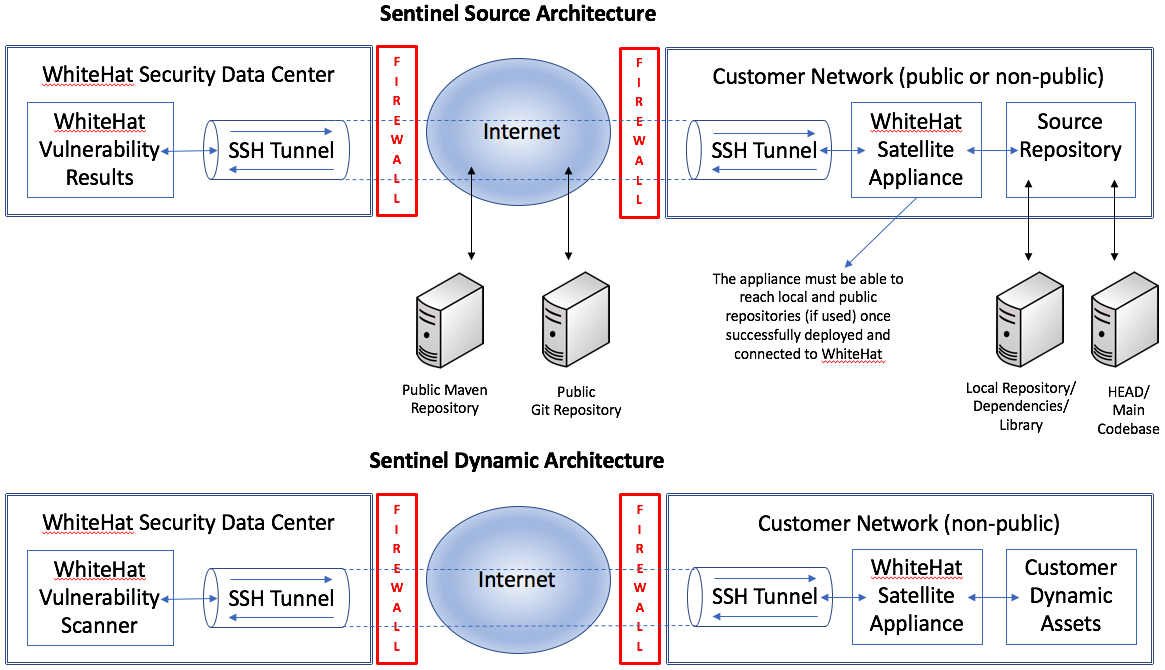
The purpose-built Sentinel Appliance will reside strategically behind the firewall, typically inside a customer demilitarized zone (DMZ).
The architecture will vary depending on whether you are using Continuous Dynamic (DAST scanning) or Sentinel Source (static scanning).
Note that DAST appliances are assigned a /24 subnet that can accommodate a total of 254 primary and associated hostnames.
Sentinel Appliance Operations
The Sentinel Appliance is a VM appliance configured by Black Duck to be deployed inside the customer’s network. It will periodically connect to Black Duck’s controller (see Installation / System Requirements for more details on the IP addresses and ports involved).
The controller authenticates with the satellite and negotiates a list of customer code bases (for Sentinel Source) and/or web sites (for Continuous Dynamic) to test. The Sentinel appliance establishes a secure encrypted SSH tunnel back to a Controller server at Black Duck. Scanning parameters are communicated via this tunnel to a scan engine that runs on the Sentinel appliance; for Sentinel Source, this includes checking out source code from the customer’s repositories and performing the analyses. The Controller can assign virtual IP addresses to the customer’s web sites so that Black Duck’s scanners can reach private RFC 1918 addresses to support Continuous Dynamic.
Continuous Dynamic uses SSH2 AES-256 key pairs; these are created when the appliance is set up. The appliance can only call one (1) IP address and then present its authentication to the receiving device. Black Duck cannot call the appliance. If the authentication fails there is no connection; the customer retains all control over what access the device has. The appliance simply opens a secure channel to Black Duck so that the scanners can route through it to your assets. Continuous Dynamic (DAST) appliances attempt to re-establish their SSH tunnel connection every hour; Sentinel Source (SAST) appliances also attempt to re-establish their tunnels hourly unless there is currently a scan running on the appliance.
All scanner traffic is transported within the encrypted SSH tunnel.
Deciding How to Host Your Sentinel Appliance
There are three options for hosting your appliance: on your premises, via AWS, or using Black Duck cloud hosting.
Black Duck Cloud Hosting
If you prefer not to host your SAST appliance yourself (which can be done either via AWS or on your own premises), you can request Black Duck to host your appliance for an additional fee. Note that assets using a Black Duck-hosted appliance should typically be accessible via the public internet. Black Duck hosting for assets available only via your internal network will require you to allow bilateral traffic between your network and Black Duck.
To request that Black Duck host your SAST appliance, please click the "Request" button under "Black Duck Cloud Hosting" on the SAST tab of the Appliance Management page, as shown:
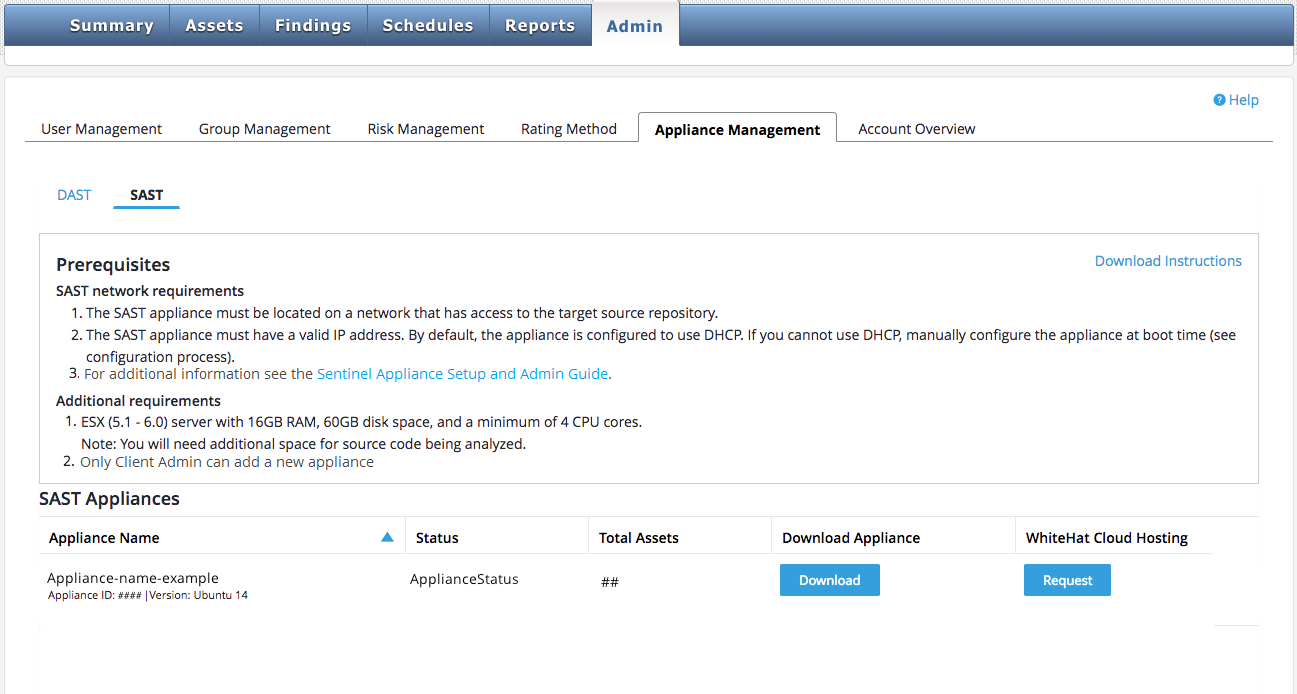
The primary benefit of requesting that Black Duck host your appliance in the cloud is that you are totally relieved from administrative duties to support the Sentinel appliance.