The Attack Vector Detail Report
The Attack Vector Details Report provides details of vulnerability instances (attack vectors) found on sites or APIs selected for Dynamic Analysis. In addition to the location and time that the vulnerability was discovered, the attack vector details include a breakdown of the exact request and response so that developers may easily replicate the problem. This report is most likely to be of interest to developers engaged in remediating a specific vulnerability.
Asset List
The Attack Vector Details Report provides a list of assets included in this report, shown below.

Issue Summary
The following table displays a breakdown of vulnerabilities by class. The table shows the Vulnerability ID, Class, Rating and Attack Vector ID.
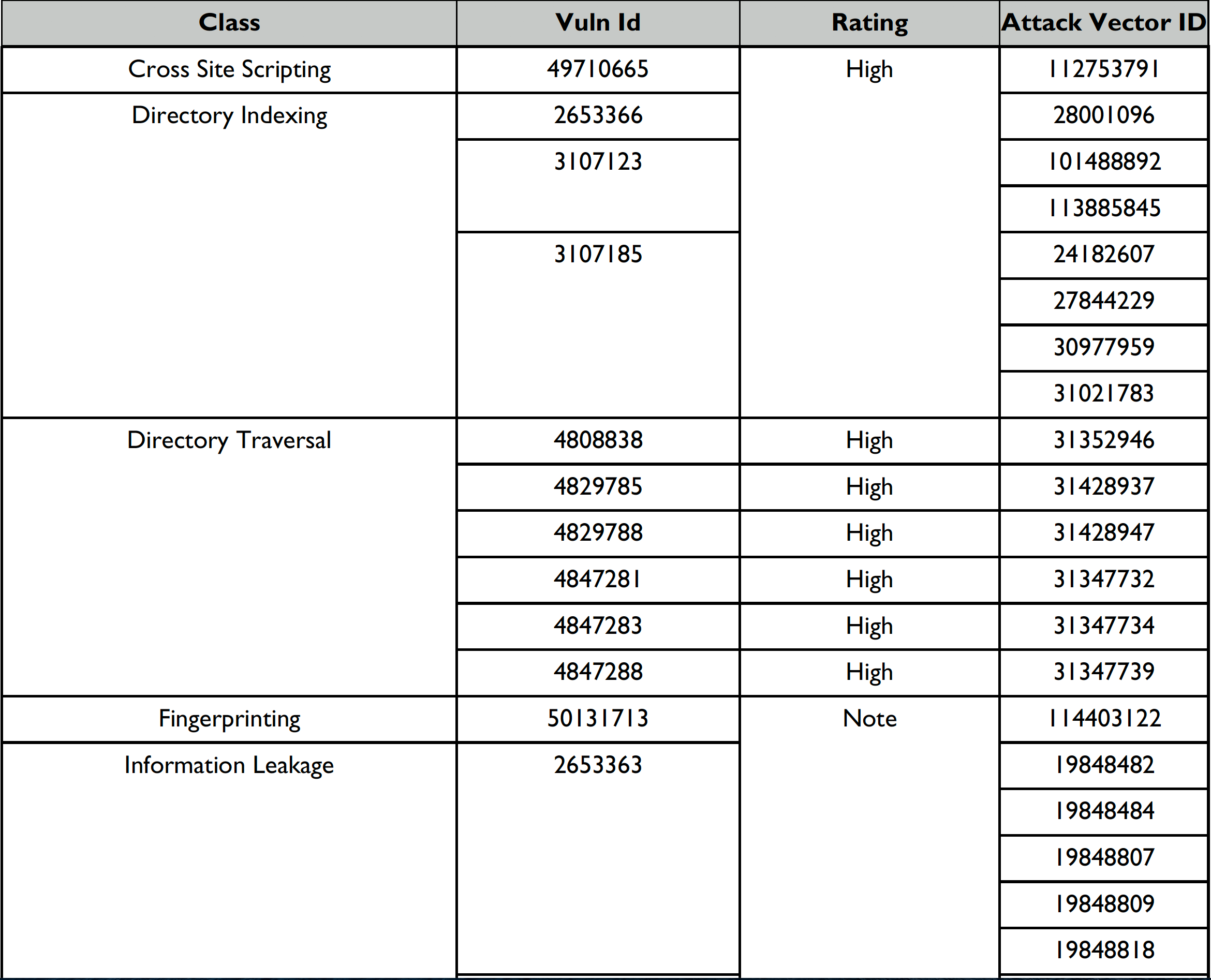
Attack Vector Details
The report provides a short vulnerability overview as shown below for each attack vector.
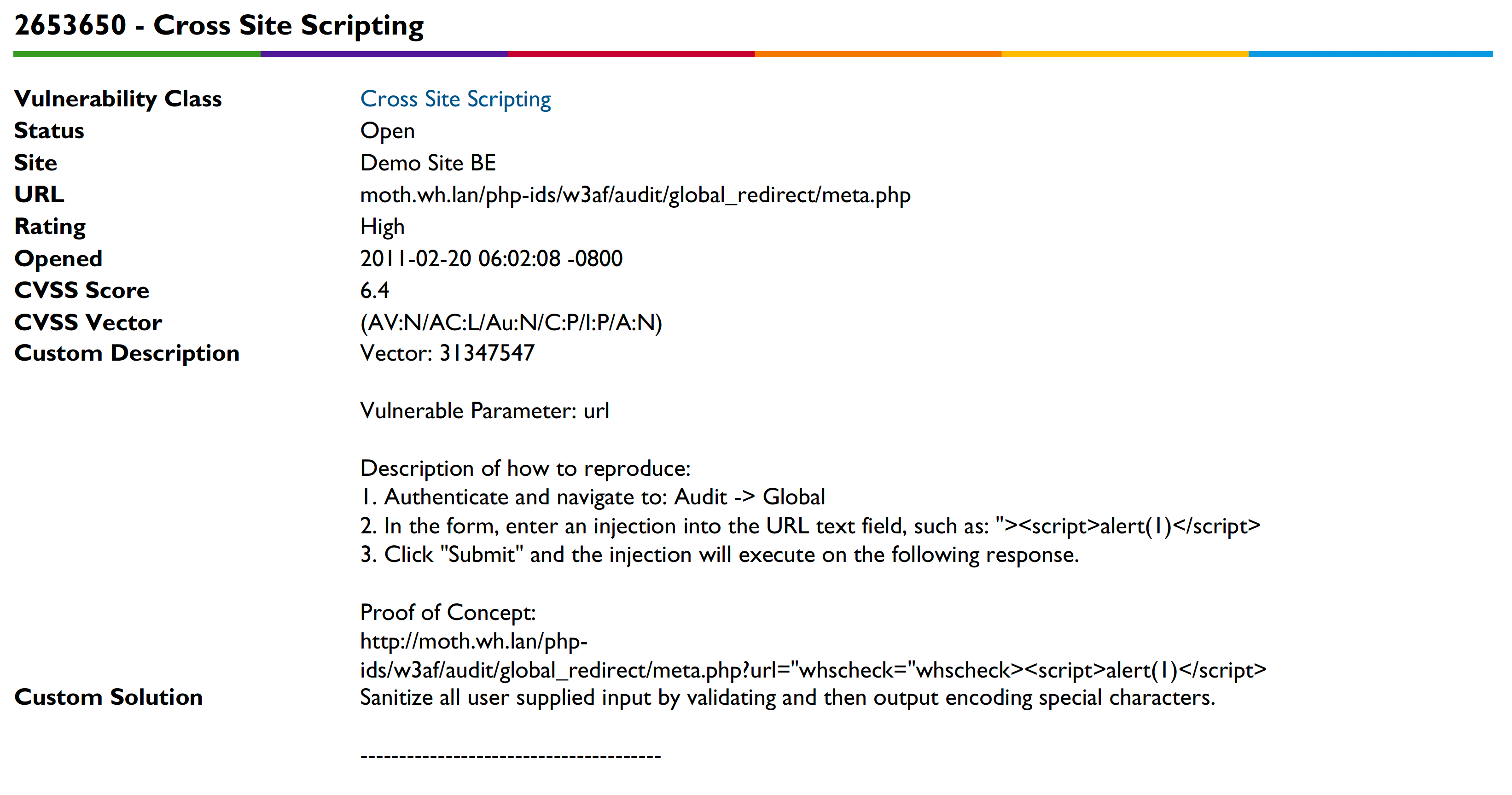
This overview is followed by the Attack Vector Details.

The attack vector details include a breakdown of the exact request and response so that developers may easily replicate the problem. (as shown below)
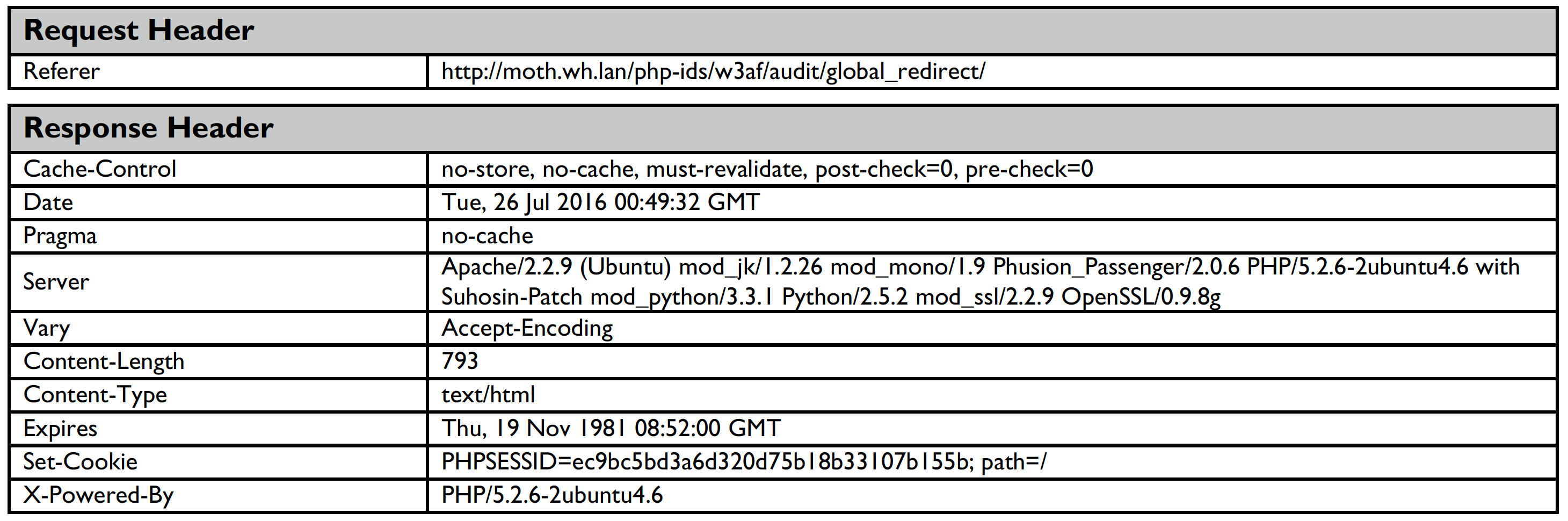
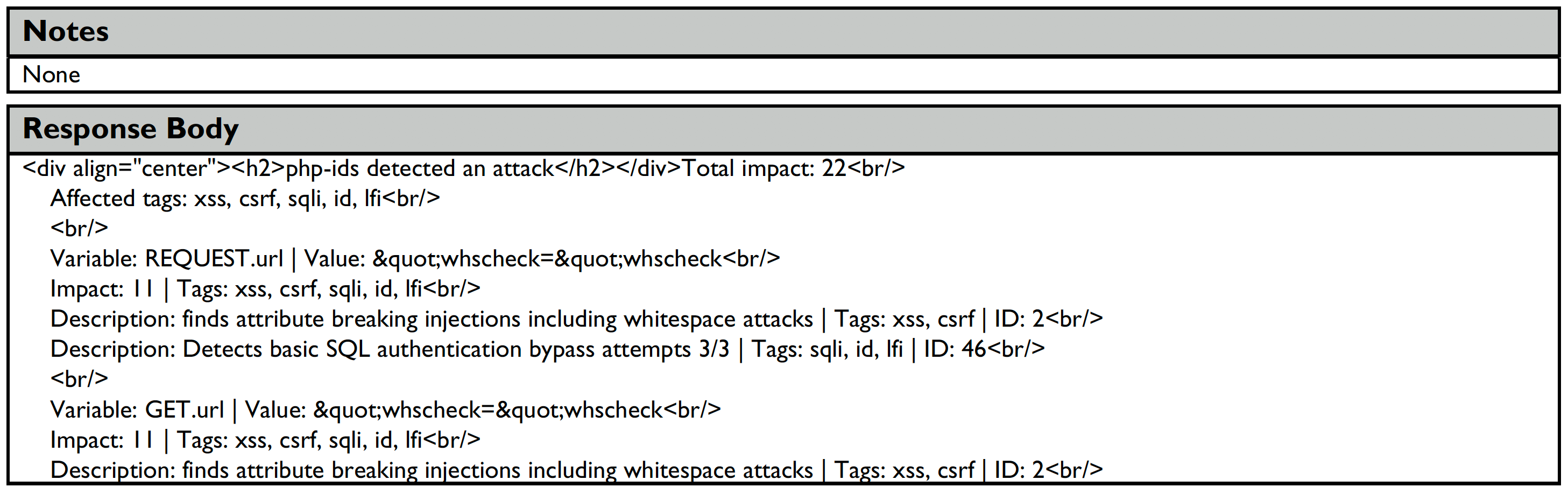
Definitions
Descriptions and Solutions for each vulnerability class detailed in the report are included. References are provided for both descriptions and solutions. A sample definition for Cross Site Scripting is shown below.
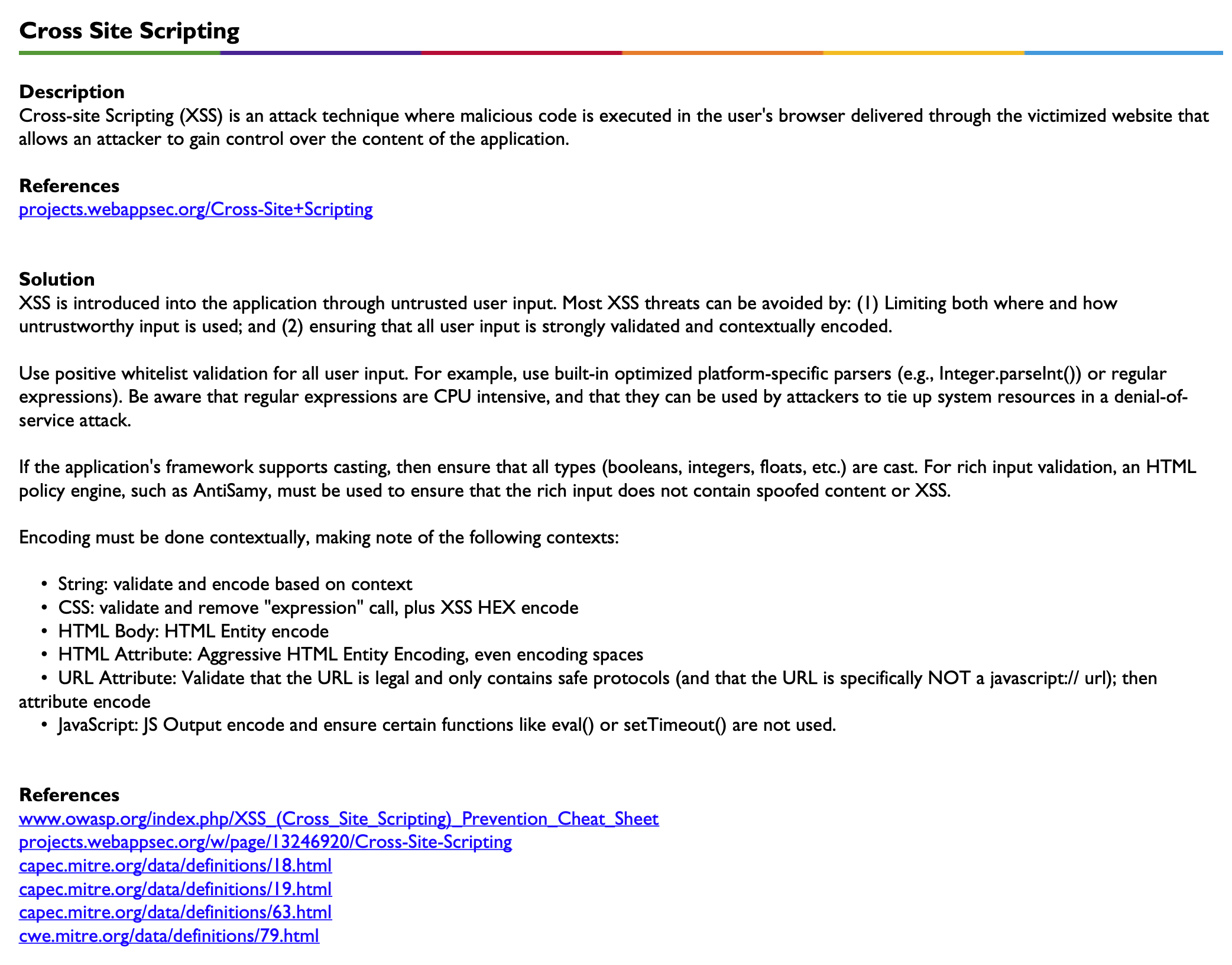
Appendix - Vulnerability Level Definitions (by Risk)
This section details how the vulnerability levels are defined, risk Levels for the Sentinel Source solution are based on the OWASP risk rating methodology, based on the standard risk model (Risk = Likelihood x Impact) with several factors contributing to the likelihood and impact. The following tables show how the vulnerability ratings are calculated in The Attack Vector Details Report.
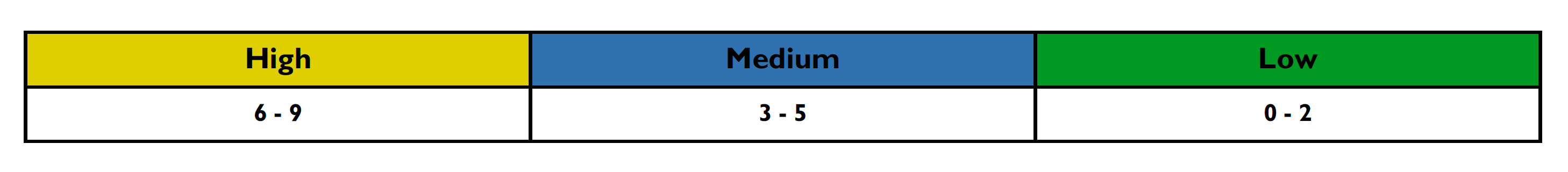
-
The Impact can be broken down into the Technical Impact and Business Impact. Technical impact considers the traditional areas of security: confidentiality, integrity, availability, and accountability.
-
The business impact stems from the technical impact and consider things such as: financial damage, reputational damage, non-compliance, and privacy violations.
After scoring the Likelihood and Impact, the Risk Rating is determined using the following table:
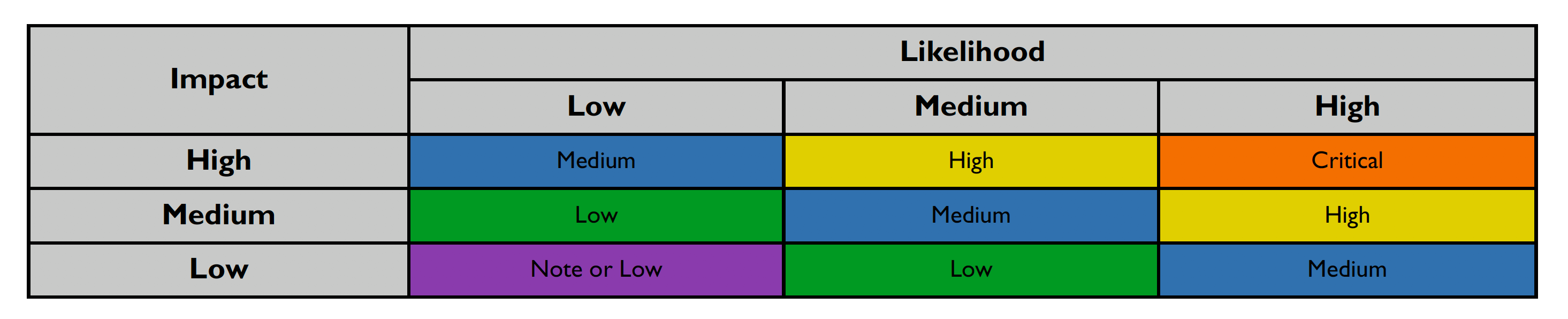
Risk ratings are defined below:
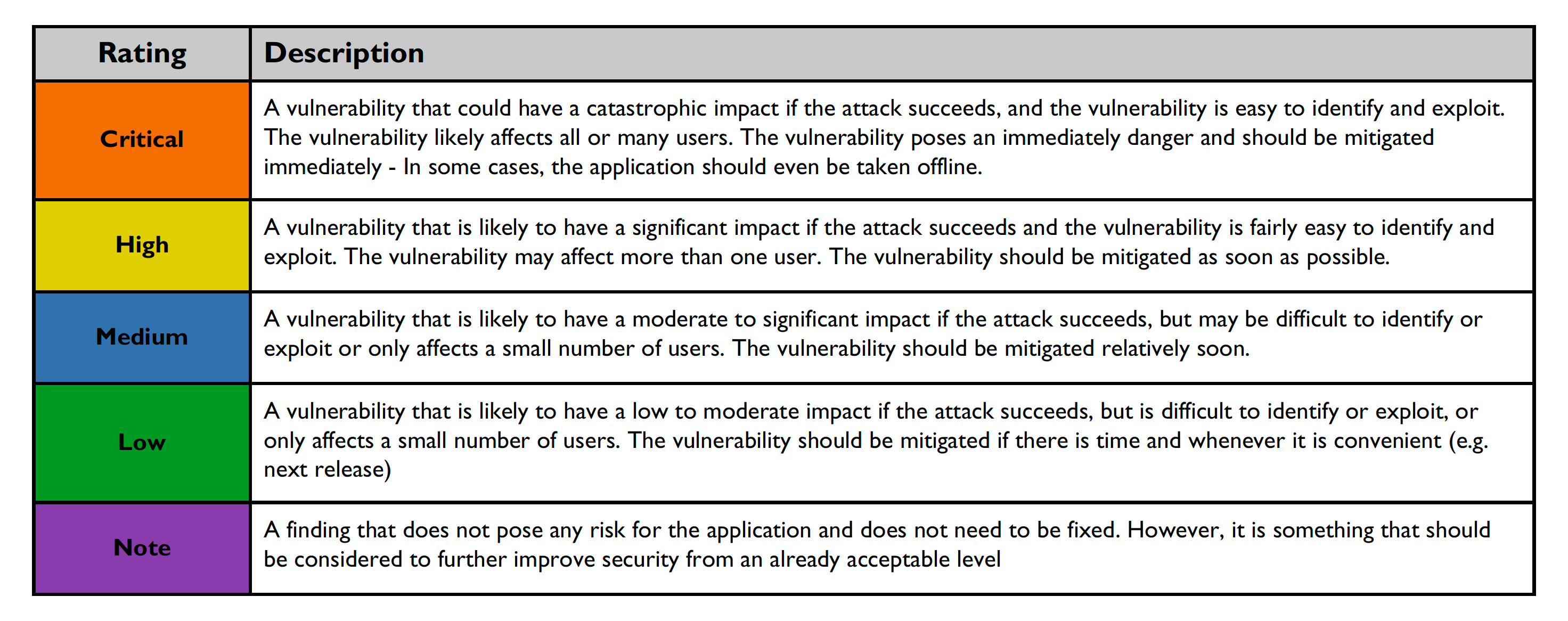
Vulnerability verification status indicated below:
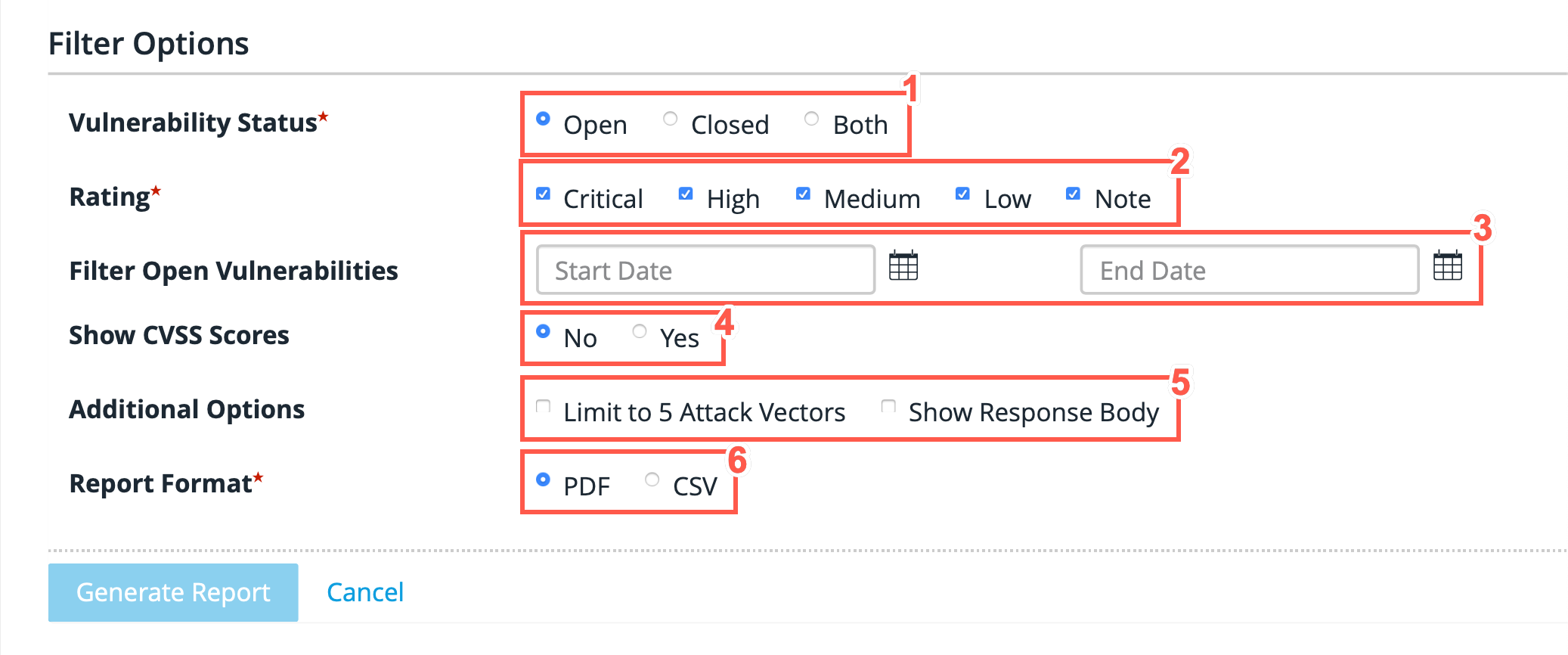
The Attack Vector Detail Report - Options
The following are some of the other attack vector detail report options to choose from:
-
Select whether you want to see Open, Closed, or Both (all) vulnerabilities.
-
Specify the severity rating level to include.
-
Filter by date.
-
Show the CVSS scores.
-
Determine whether you want to Limit to five Attack Vectors or show the Response Body in the report.
-
Choose to generate the report as a PDF or as a CSV file
For more information on generating reports, see the following Report Section.
The Attack Vector Detail Report - Selection by Groups
You can also select sites based on groups. When you have made your selections and clicked on Generate Report, the report will return to you as a pdf file. For each vulnerability class included in the report, you will first see the description and solution for the vulnerability, and then the details of the attack vectors.