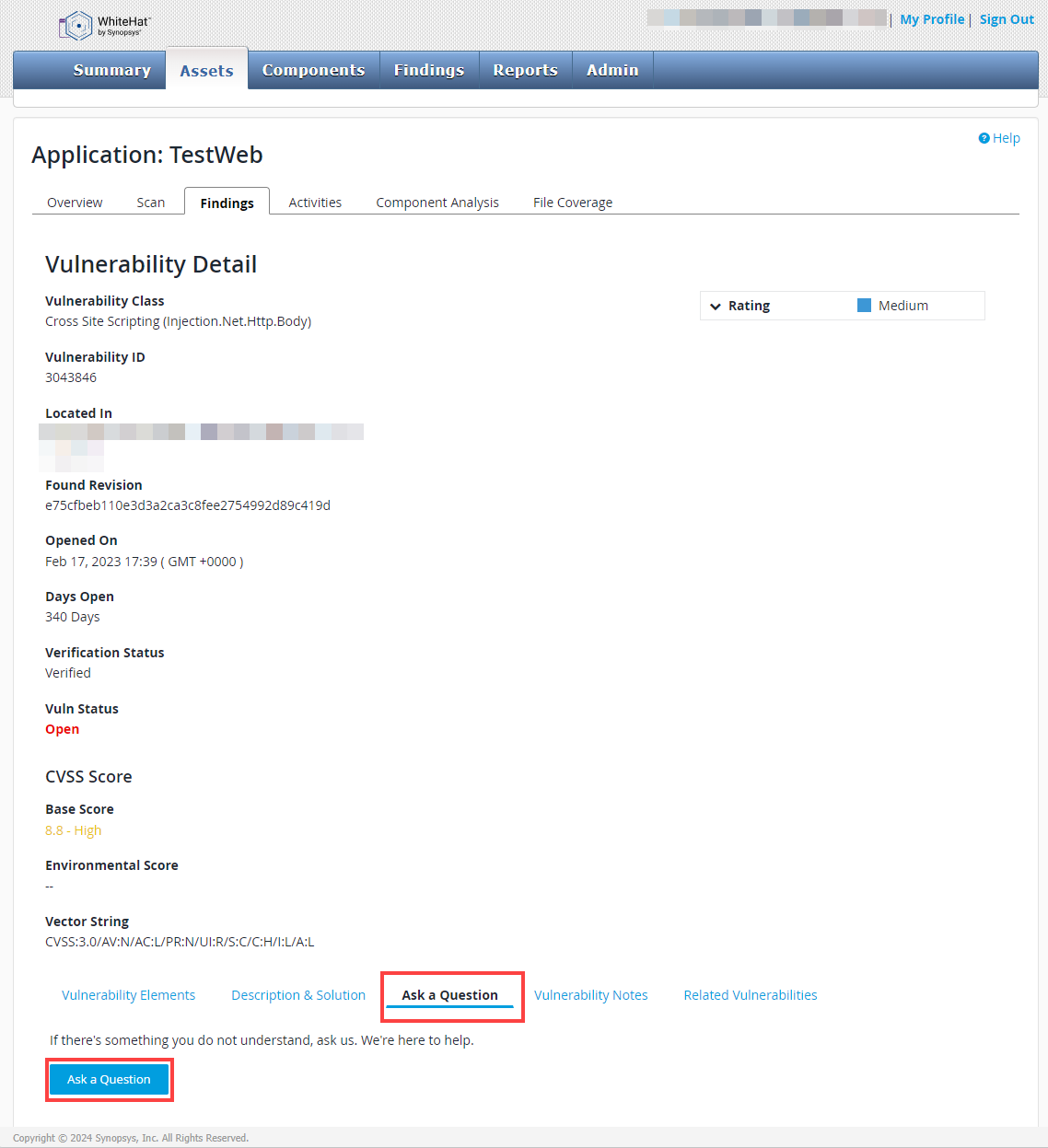
The Vulnerability Detail Screen: Applications
The application Vulnerability Detail screen is available from the Summary tab, under the Assets tab, and the Findings tab. It gives you exact details about a specific vulnerability. The Vulnerability Detail is quite large, so this is a summary of the top of section of the screen:
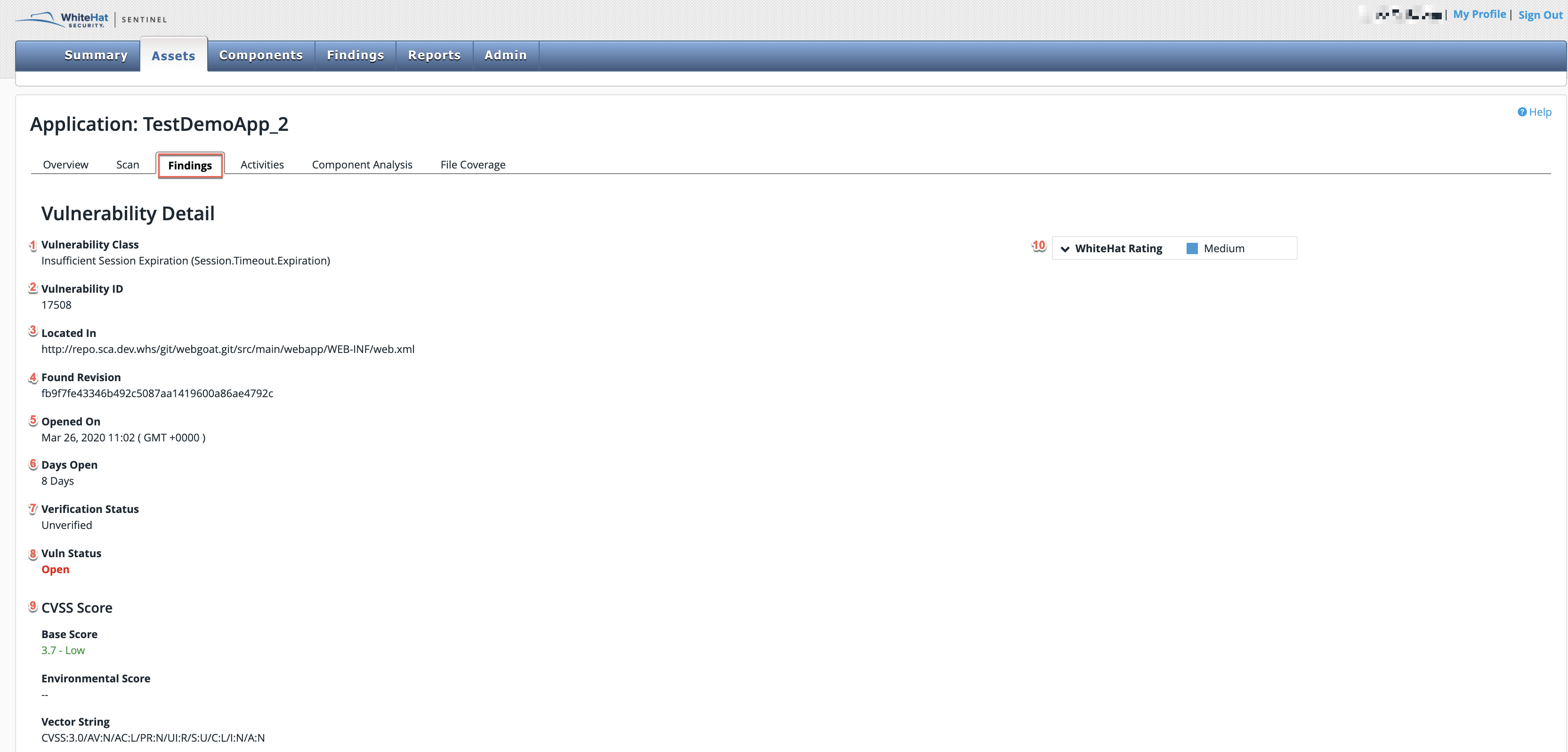
| Field No. | Field Name | Description |
|---|---|---|
1 |
Vulnerability Class |
This is the name of the general type of vulnerability — for example, cross-site scripting or sql injection. |
2 |
Vulnerability ID |
This is the unique Continuous Dynamic ID for this specific vulnerability. |
3 |
Located In |
This gives the path to the vulnerability. (This will be the URL for a site or the repository path for an application. Applications with unpatched library vulnerabilities will include specific location information if the customer is using a package manager for which Sentinel Source supports specific locations.) |
4 |
Found Revision |
This is the revision where the vulnerability was found during scan. This may or may not be the actual revision where the vulnerability was introduced by the developer, since there can be many revisions submitted in a single day. |
5 |
Opened On |
This is the date the vulnerability was reported. |
6 |
Days Open |
This is the number of days the vulnerability is or was open. The number is rounded down. |
7 |
Verification Status |
This indicates whether the vulnerability is certified (verified) by Black Duck or not. |
8 |
Vuln Status |
This is open, closed, accepted, mitigated, or invalid. (Please see Vuln Status.) |
9 |
CVSS Score |
The Common Vulnerability Scoring System (CVSS) is a free and open industry standard for assessing the severity of computer system security vulnerabilities. CVSS attempts to assign severity scores to vulnerabilities, allowing responders to prioritize responses and resources according to threat. |
10 |
Black Duck Rating |
Classification of the threat posed by the vulnerability, based on Black Duck research (Low, Medium, High and Critical). |
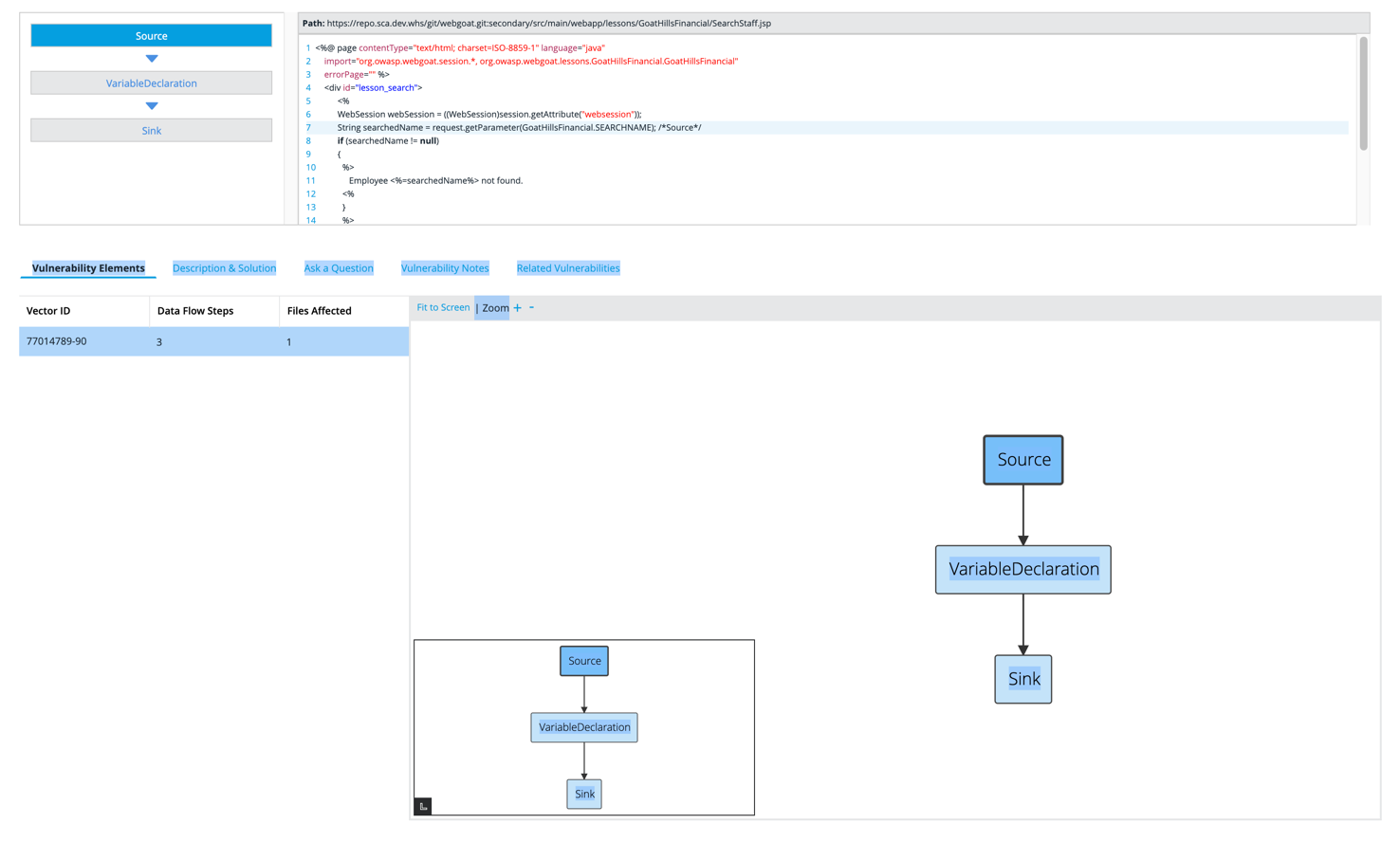
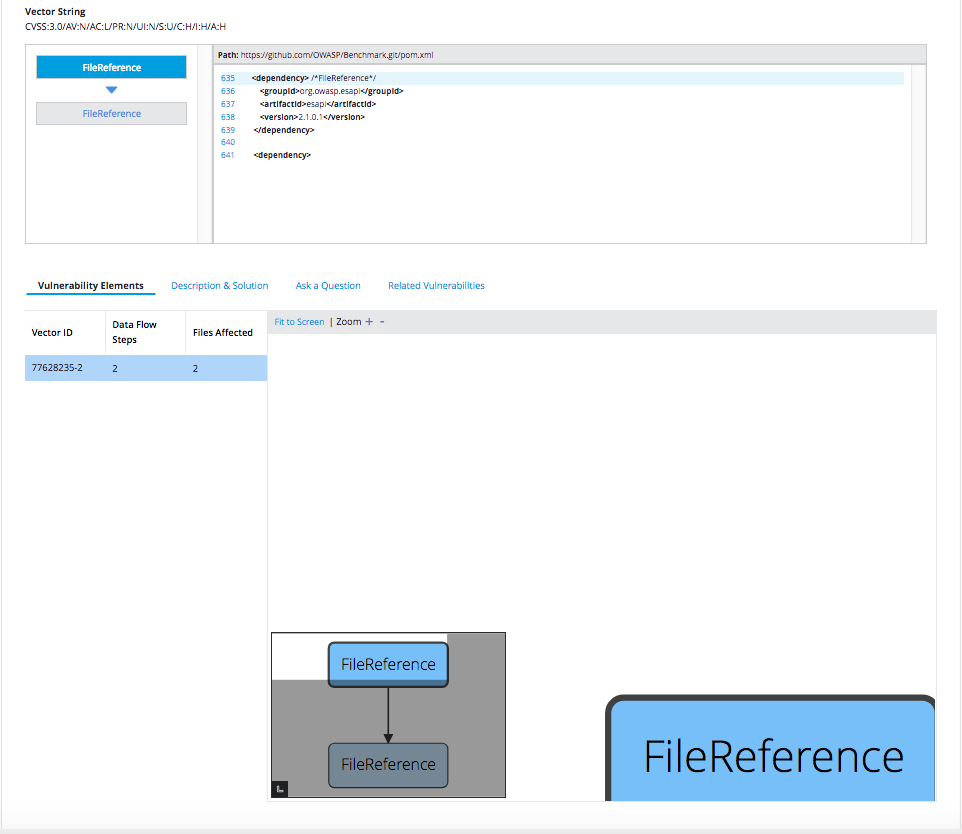
Vulnerability Details Tabs
In the lower sections of Vulnerability Details screen, there are a number of tabs that allow the user to drill in deeper into the finer detail about each vulnerability.
Vulnerability Elements
This provides the vulnerability elements, such as the Source, Sink and Variable Usage, etc.
Description & Solution
If a recommended patch or remedial steps are available, they will be provided in this tab. Here you can review remedial steps and download recommended patches, as they relate to the specific vulnerability in question.
Ask a Question
If you need more information about the vulnerability than is available in the Description & Solution tab, you can use the Ask a Question tab for clarification. Questions submitted here are routed directly to our engineers, bypassing the Black Duck Community.
Ask a Question
To ask a question using the Vulnerability Management functions, perform the following steps:
-
Click Findings.
-
Select a Vuln ID from the Vulnerability Management page:
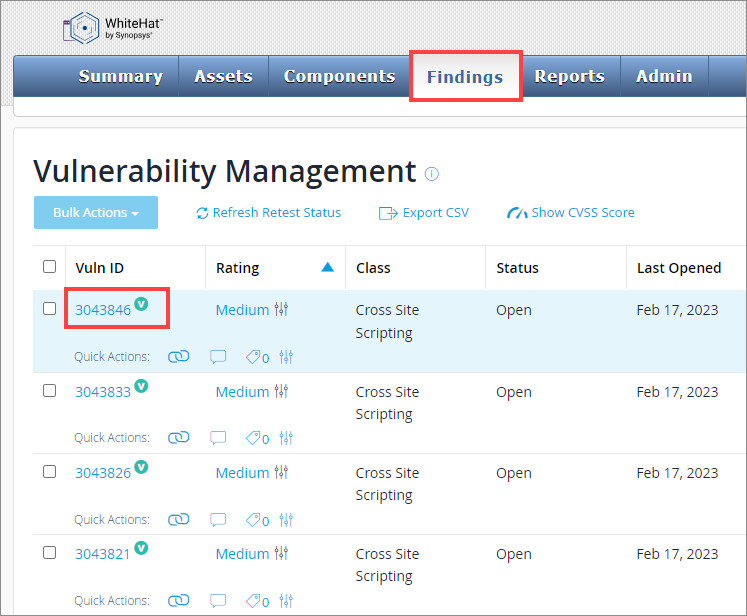
-
Select Ask a Question.
-
Click the Ask a Question icon.
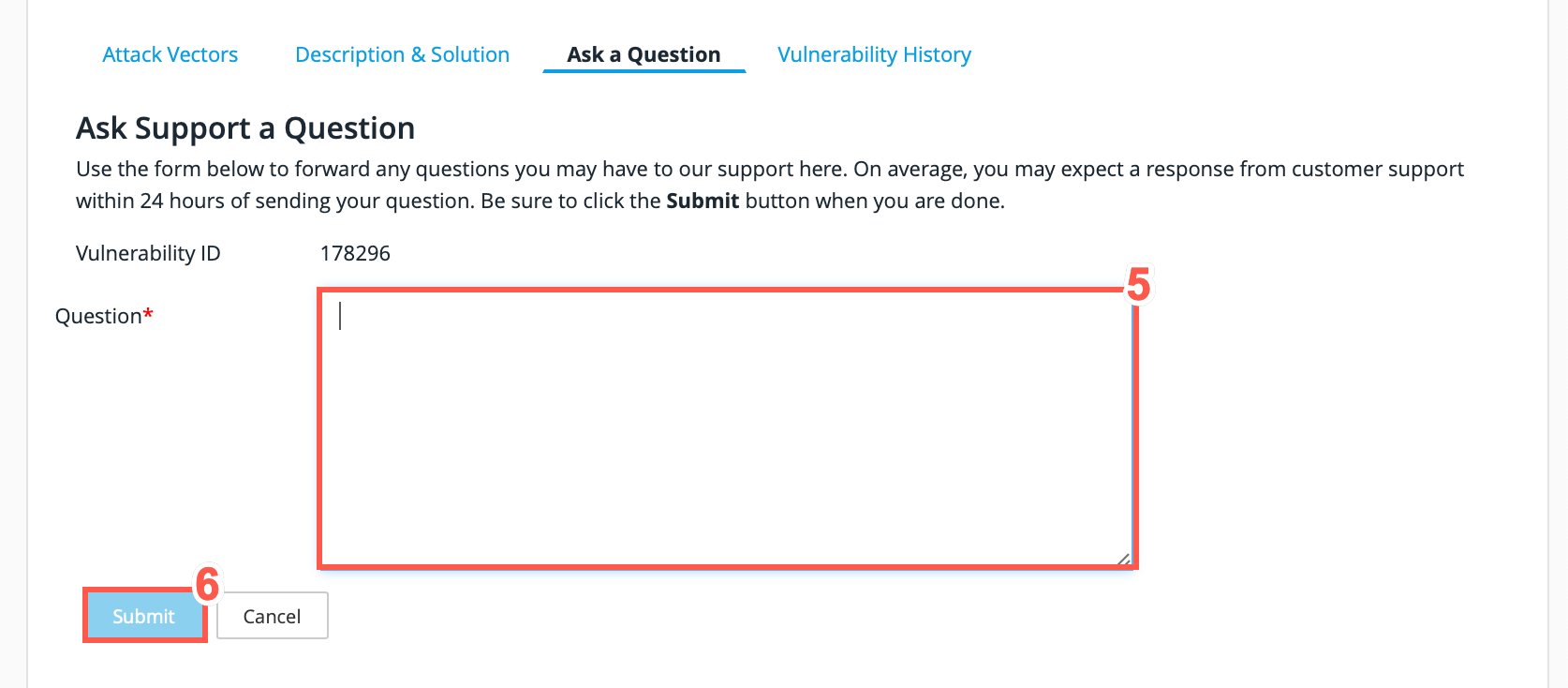
-
Type a Question in the text field provided.
-
Click Submit to send your question to the Threat Research Center.
| Previous questions and responses can be reviewed in the Ask a Question section. |
Vulnerability Notes
Users can write notes here in order to keep a record of remedial steps taken and to communicate with other team members about the vulnerability.
Related Vulnerabilities
If there are similar vulnerabilities elsewhere in this application (or in other applications that this viewer has permissions for), they will be listed in this tab, making it easier for developers to resolve all related vulnerabilities in a systematic and consistent way.
| For more information on dependency errors, refer to Dependency Errors in Java or Dependency Errors in C#. |